Internet has undoubtedly been one of the most significant developments in humanity’s technological journey since the industrial revolution. Rapid advances in telecommunication, especially wireless coupled with software application development, has led to the proliferation of internet to almost all facets of human activity. The ‘Internet

of Things’ or ‘IoT’ amalgamates the strengths of network, wireless, miniaturised hardware, software, and cloud to create an even greater medium that pushes the frontiers of day-to-day usage of technology in a multitude of facets of human life. Simply put, the IoT is a computing concept of physical objects being connected to the internet, being able to identify themselves to other devices, and being able to intelligently exchange data through a variety of media. IoT thus creates an ecosystem wherein just about anything, and not just present-day devices such as laptops, smart phones, tablets, wearable digital devices etc., can be connected and can communicate in an intelligent manner. The result thus is a physical world transforming into a gigantic digital information system with application in manufacturing, R&D, smart cities, smart homes, smart campuses, critical infrastructure, transportation, computing, agriculture, defence, security & surveillance, or in any other sector. This has led to the emergence of new applications and business models. However, the IoT, like all digital technologies that make it up, is fraught with vulnerabilities and potential risks.
Growth of IoT
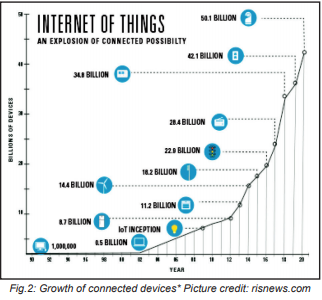 We see connected devices increasing in our life day by day. By qualified estimates, at present (2019) there are approximately 7 billion inter-connected devices. This number is expected to increase to about 29 billion by 2022, of which approximately 18 billion will be related to IoT. Between 2016 and 2022, IoT devices are appreciated to increase at a CAGR of 21 percent, driven by new use cases, miniaturization of hardware, increase in computing power, ICT (4G/ 5G), lowering data cost, low energy consumption etc. It is expected to be 50 billion connected devices by 2025 with a total of 100 billion connections in public utilities, transportation, manufacturing, healthcare, finance, agriculture, personal and domestic devices, and in other industries. Corporate security has been one of the early adopters of IoT.
We see connected devices increasing in our life day by day. By qualified estimates, at present (2019) there are approximately 7 billion inter-connected devices. This number is expected to increase to about 29 billion by 2022, of which approximately 18 billion will be related to IoT. Between 2016 and 2022, IoT devices are appreciated to increase at a CAGR of 21 percent, driven by new use cases, miniaturization of hardware, increase in computing power, ICT (4G/ 5G), lowering data cost, low energy consumption etc. It is expected to be 50 billion connected devices by 2025 with a total of 100 billion connections in public utilities, transportation, manufacturing, healthcare, finance, agriculture, personal and domestic devices, and in other industries. Corporate security has been one of the early adopters of IoT.
Corporate security in the age of IoT
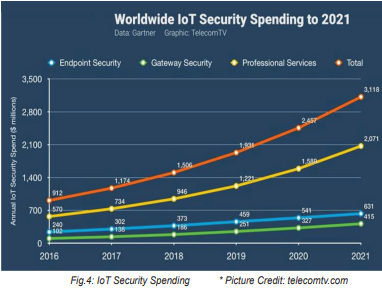
The greatest challenge to corporate security during the past decade has been cybercrime – primarily distributed-denial-of-service (DDoS), malware, ransomware and data breach/ theft. Ransomware damage costs exceeded $5 billion in 2017 alone, 15 times the cost in 2015. It has been qualified that cybercrime costed the world $3 trillion in 2015, and that this figure would increase to $6 trillion annually by 2021 with a major attack vector being targeting to IoT. Gartner has predicted that by 2020, approximately 25% of all attacks on enterprises will target IoT. Accordingly, global spending on cybersecurity products and services are predicted to exceed $1 trillion cumulatively over 2017 to 2021, with a 12-15 percent year-over-year cybersecurity market growth through 2021. This may, however, not suffice to protect the new way of life through IoT.
Mitigating vulnerabilities of IoT
A typical IoT architecture is depicted below. It is easy to infer that each stage or layer of the architecture can be exploited by nefarious-intentioned attackers. Vulnerabilities could cause, for example, an attacker taking control of a visitor management system, or disrupting a supply chain, locking down a manufacturing facility, or shutting down a critical utility of a city or campus, or even scarier scenarios.
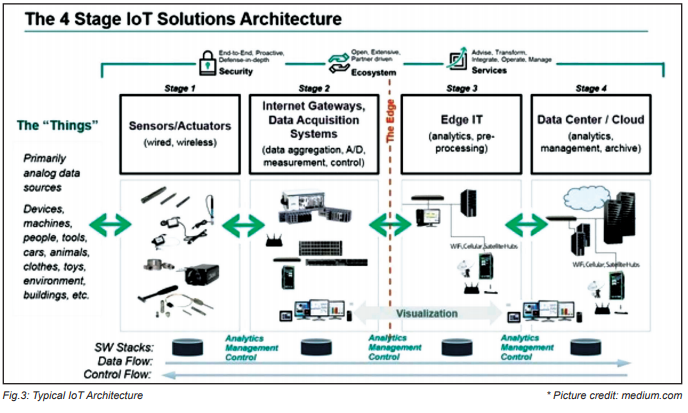
Mitigating the principal technical vulnerabilities would entail the following:
- Strengthen the network: Protection and security of the network connecting IoT devices to back-end
 systems on the internet is critical. However, IoT network security is more challenging than traditional network security as there is a wider range of communication protocols, standards and device capabilities – all of which pose significant issues and increased complexity. Key capabilities would include traditional endpoint security features such as anti-virus, anti-malware, firewalls, and intrusion prevention and detection systems.
systems on the internet is critical. However, IoT network security is more challenging than traditional network security as there is a wider range of communication protocols, standards and device capabilities – all of which pose significant issues and increased complexity. Key capabilities would include traditional endpoint security features such as anti-virus, anti-malware, firewalls, and intrusion prevention and detection systems. - IoT device authentication: Unlike regular enterprise networks where the authentication process involves a human entering an access credential, most IoT authentication scenarios (such as embedded sensors) are machine-to-machine based, without any human intervention. Therefore, designers/ users must have the ability to authenticate an IoT device including managing multiple users of a single device (such as a connected car), ranging from simple static password/ Pins to multi-factor authentication, digital certificates, biometrics etc.
- Encryption key life-cycle management: Encrypting data at rest and in transit between IoT edge devices and back-end systems using standard cryptographic algorithms help maintain data integrity and prevent data sniffing by hackers. The wide range of IoT devices and hardware profiles limits standard encryption processes and protocols. Further, all IoT encryption must be accompanied by equivalent full encryption key lifecycle management processes, since poor key management will reduce overall security.
- Robust IoT PKI: The hardware specs for IoT devices manufactured by different OEMs may limit or prevent their ability to utilize public key infrastructure (PKI). Notwithstanding, digital certificate, and cryptographic key, and life-cycle capabilities including public/ private key generation, distribution, management and revocation are essential. Towards this, digital certificates could be securely loaded onto IoT devices at the time of manufacturing, and then activated/ enabled by third-party PKI software suites. Alternately, the certificates could be installed post manufacture.
- AI, ML in IoT: IoT security analytics will increasingly be required to detect IoT-specific attacks and intrusions that are not identified by traditional network security solutions such as firewalls. Here, machine learning, artificial intelligence and big data could provide predictive modelling and anomaly detection while collecting, aggregating, monitoring and normalizing data from IoT devices so as to provide actionable alerts on specific activities, or when activities fall outside established policies.
- API security: API security will be essential for protecting the integrity of data transiting between edge devices and back-end systems to ensure that only authorized devices, developers and apps are communicating with APIs, as well as for detecting potential threats and attacks against specific APIs.
Looking ahead
More devices are being IoT enabled – means more complex is the IoT ecosystem. Further, more data is being collected than ever before and being stored at various places, but there is no clear regulation or direction on how this data should work. ‘Trust’ – that is one of the pillars on which the internet was formed has often suffered. Consumer confidence is likely to define an organization’s success in the IoT world, with security playing a huge part in that. If government sets regulations, faith can be restored and built into the security of the IoT ecosystem. Decision makers in corporates must view IoT with equal measure of optimism as well as scepticism. However, given the huge potential of monetization of IoT-driven business opportunity, organizations must see a long-term goal that can be achieved through a secure IoT platform. A partnership alongside an IoT security specialist then becomes an obvious option, and vital. Partnerships could be formed due to the partners have the IoT skills/ knowledge that organizations do not, to facilitate and speed up IoT deployment. Corporate security, which moved from the physical realm to the digital realm, would increasingly graduate to an integrated and interconnected realm wherein IoT would be used to pre-empt and prevent mishaps by harnessing technology rather than being reactive.

An alumnus of IIM, Ahmedabad and Jamnalal Bajaj Institute of Management Studies, Mumbai, Sandeep Sinha serves as the Director – Defence, Strategic Projects of MitKat Advisory Services Ltd. He heads Mitkat’s operations in North and East India. He has vast experience of consulting in the realm of security risk management across Industry sectors in India and abroad, Homeland Security and Smart Cities, and Ministry of Defence’s very large critical infrastructure project of strategic nature. He also represents MitKat at industry associations of repute. Views expressed are personal.
-Sandeep Sinha,
Director – Defence & Strategic Projects, Regional Head of Operations-North & East, MitKat Advisory Services ltd.