
Anil Puri
CMD, APS group
A first generation serial entrepreneur, thought leader and an action catalyzer rolled into one – Anil Puri is a rare combination of a visionary, an innovator and a strategic thinker. He has used this combination to innovate and implement on-ground many new business ideas. His rich experience in various businesses has enabled him to nurture & mentor innovative ideas and scale them up.
Introduction
In its quest for digitalization, India has become an easy target for cyberattacks due to poor cybersecurity. The frequency and targets of cyberattacks on India are becoming increasingly alarming.
The high-profile ransomware attack on Delhi’s All-India Institute of Medical Sciences (AIIMS) on 23 Nov 2022 exposed gaping holes in the country’s cybersecurity infrastructure causing disruption of online services that lasted over two weeks thus bringing to fore the critical infrastructure vulnerability. India’s nodal cybersecurity agency Computer Emergency Response Team (CERT-In) found in its investigation that five AIIMS’ servers were compromised during the cyberattack and nearly 1.3 terabytes of data were encrypted by hackers. But it was hardly an isolated incident. Industry data shows that 2022 has been the worst year so far for India when it comes to cyberattacks – a problem that has only grown with increasing digitalization. Ransomware attacks in India have increased significantly and in an unprecedented numbers. One of the most distinguishing aspects in 2022 was the involvement of state actors. India saw the highest number of cyberattacks on government agencies in 2022. Experts believe that state-sponsored hackers will go after cloud services in 2023 due to growing digital transformation as companies migrate more of their attack surface to these cloud managed services.
articles like these, get access to Mint Premium at 25% discount
India’s Cyber Vulnerabilities
In 2019, CERT-In handled close to 3,94,499 incidents in total, in which it suggested remedial measures for organizations and shared notes on cyber threats and vulnerabilities. In the same year, CERT-In issued 204 security alerts and 38 advisories. The number of incidents handled by CERT-In surged in 2020 to 11,58,208, a near-tripling over the previous year. This surge continued in 2021, which saw 14,02,809 incidents, a 21 per cent increase.
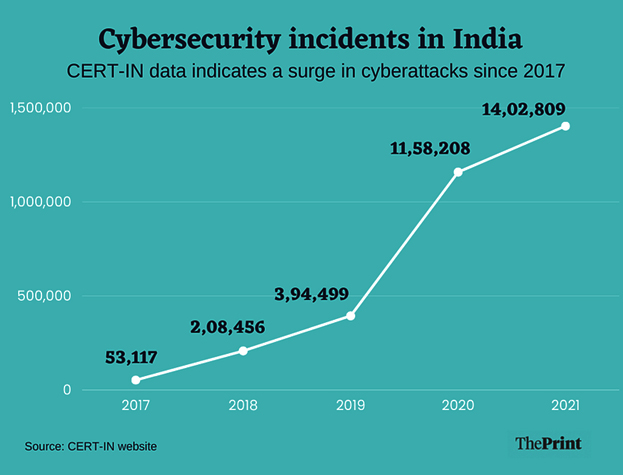
The matters CERT-In looks into include website intrusion and malware propagation, malicious code, phishing, distributed denial-of-service (DDoS) attacks, website defacements, unauthorized network scanning or probing activities, ransomware attacks, data breaches and vulnerable services.
In this backdrop, what will the government and companies do differently in the coming year?
As the government readied its legislation on cybersecurity, numerous industry-wide surveys and sector experts say that 2023 will see companies spending significant amounts to secure their digital systems from attacks. CERT-In has also laid out a standard operating procedure for data breaches wherein companies and other organizations are supposed to inform the government of any breach within six hours, although this move has received a mixed reaction since compliance may be challenging.
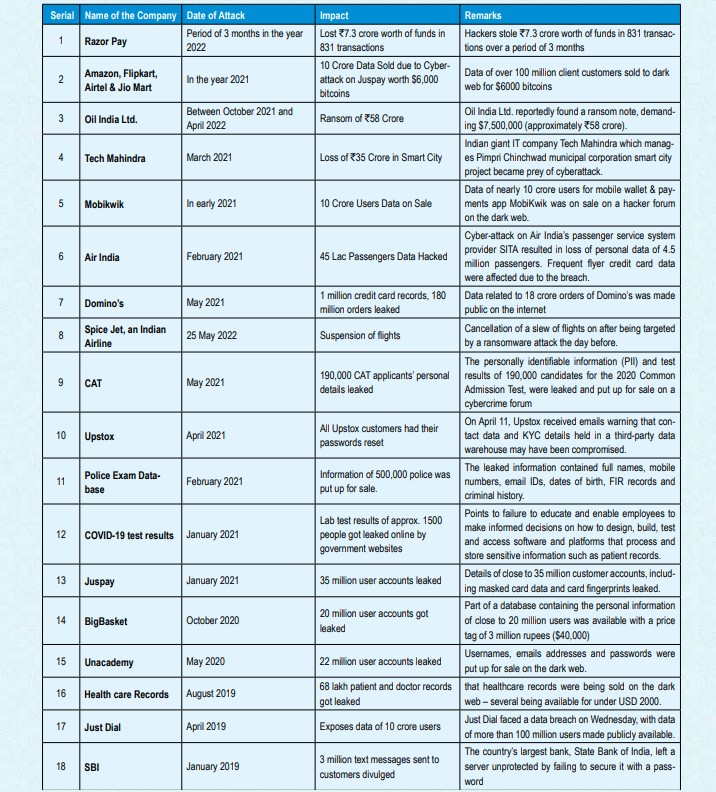
Chronological history of Cyber Attacks on India in last three years.
In another report, CloudSEK also reported an uptick in the number of cyberattacks on banking and financial sector. The report, however, identified different patterns when compared between 2021 and 2022. The attacks in 2021 were on a global scale with an equal focus on North America whereas the events in 2022 saw a shift towards Asia. Within Asia, India stood pretty high, with the report characterizing India as ‘the new found hotbed for cyberattacks in Asia.’ The Banking Finance Services and Insurances (BFSI) has been identified as the most targeted sector in the FY 2021-2022. A comparison of the number of cyber events in 2021 and 2022 reveal that the US, India, and Brazil continue to be among the most targeted states.
Response of the Nodal Agencies
According to government data, in 2019, total number of cyber security incidents tracked by Indian Computer Emergency Response Team (CERT-In) was 3,94,499. The number spiked to 11,58,208 in the year 2020 and further increased to 14,02,809 in 2021. This year, as many as 6,74,021 cyber security incidents were reported till June.
Cyber Attack which has put All India Institute of Medical Sciences (AIIMS), Delhi’s servers out of order on November 23 is yet to be resolved completely. Multiple agencies have been looking into the Cyber Attack at the crucial installation of the country. While a case has been registered, the CERT-IN, Delhi Police and other investigating agencies are probing the incident. On December 1. 2022, cyber attackers briefly hacked the Ministry of Jal Shakti’s Twitter handle, the second major Cyber Attack on a government site.
A Parliamentary Standing Committee in its report this year observed that there is a significant surge in cyber incidents and cyber security breaches and it is imperative that capabilities and resilience of the country to deal with imminent dangers on cyber space are enhanced proportionately.
Cyber Security has to remain at the forefront of agenda/ priority items for the Ministry and no fund crunch should come in the way of ensuring a safe ecosystem as far as the Cyber world is concerned. In fact the Committee feels that the Ministry must dovetail their efforts to achieve a more secured cyber world especially in the wake of renewed challenges in this domain. The Committee, therefore, recommends that funds for cyber security may be increased on a year on basis to forestall any failures in this domain for sheer lack of funds. The report also cited lower fund utili zation with respect to CERT-in, National Cyber Coordination Centre (NCCC) and data governance.
“So far as the underutilization of funds under the head is concerned, an amount of Rs. 216 crore had been allocated in BE (Budget Estimate) stage during 2021-22, which was reduced to Rs. 213 crore at RE (Revised Estimate) stage and actual utilization till January, 2022 has been 98.31 crore only,” said the report. As per Information Technology Ministry, the government is operating an automated cyber threat exchange platform for proactively collecting, analyzing and sharing tailored alerts with organizations across sectors for proactive threat mitigation actions by them. The Government has issued guidelines for Chief Information Security Officers (CISOs) regarding their key roles and responsibilities for securing applications/ infrastructure and compliance. Besides, all the government websites and applications are audited with respect to cyber security prior to their hosting. The auditing of the websites and applications is conducted on a regular basis after hosting also. Moreover, the government has empaneled 97 security auditing organizations to support and audit implementation of Information Security Best Practices.
Global Canvas
With the borderless cyberspace coupled with anonymity, along with rapid growth of the Internet, rise in cyber security incidents is a global phenomenon. India, US, Indonesia, and China accounted for 45% of total cyberattacks on government agencies worldwide in the second half of 2022, according to a report by cybersecurity firm CloudSek. The number of attacks on government agencies were up 95% year-on-year, the report claims. India was the most targeted country in 2022 as attacks on government agencies more than doubled. CloudSek attributed this to an increase in activities of Malaysia-based hacktivist group Dragon Force, which ran campaigns such as OpIndia and OpsPatuk against India in retaliation to the controversial comments by an Indian politician on Prophet Mohammed. Another hacker group Khalifah Cyber Crew intensified attacks on India in protest against alleged ‘Muslim discrimination’ by the government, the report said.
Hacktivism is a form of cyberattack where the hacker’s motivation is not financial gains but to promote a political agenda or protest against certain policies. Last year, attacks on China also increased due to its aggressive stance towards Taiwan and the Uyghur community. Attacks on government agencies in China declined to 4.5% of all attacks from 13.10% last year. On the other hand, in India, US, and Indonesia, the share of all attacks grew from 6.3% to 13.7%, 7.4% to 9.6%, and 4.6% to 9.3% respectively. Attacks on Russia increased 600% in 2022 in retaliation to its invasion of Ukraine, making it the fifth most targeted country. In 2022, hacktivism accounted for 9% of the cyberattacks on the government sector. In addition to hacktivism, government agencies in India are also increasingly being targeted. CloudSek also found that ransomware groups were very active and accounted for 6% of the attacks on governments.
LockBIT, which provides ransomware-as-a-service (RaaS) was the most prominent ransomware operator. Its targets this year include government agencies in the US, Canada, and Italy. In November 22, a Russian national was arrested in Canada for alleged involvement in LockBIT ransomware campaigns in the US. The ratio of government-sponsored attacks has also multiplied; however, there is no exact figure for this increase since these attacks are mostly untraceable. As per CloudSek , this growth can be primarily attributed to the advent of RaaS models.
Cyberattacks on government agencies are not new. Many of these attacks are state sponsored and are aimed at stealing sensitive information or cripple critical infrastructure of other countries. Indian entities are often targeted by hacker groups with links to China. Similarly, many of the attacks on US agencies often originate from Russia or North Korea. According to IBM’s ‘Cost of Data Breach Report 2022, the average cost of data breaches in the government sector has increased from $1.93 million in 2021 to $2.07 million this year.
Data protection Bill and CERT-In rules. Some suggestions
India’s IT ministry has come up with the Digital Personal Data Protection Bill, 2022, defining some roles of data fiduciaries and introducing appellate committees that will deal with redressals and grievances. Many have termed it a ‘step in the right direction’ to ensure data security. The law, alongside CERT-In rules, has been part of core policy discussions in India. As mentioned earlier, the rules now require companies to report cybersecurity incidents within six hours. While this seems stringent, it might not be practical for compliance.
The CERT-In directions mandating reporting of cyber security incidents within six hours was perhaps the most significant development in the cybersecurity domain this year. I’m surprised this has not been challenged since it is onerous to comply with and operationally very difficult to implement. The tightest global equivalent for reporting cybersecurity incidents is 72 hours. The suggested way forward could be the prescription of a ‘cybersecurity insurance. This could go a long way in addressing the issue.
“The other challenge is how monetary loss owing to a cybersecurity incident is remediated. Mandating cybersecurity insurance for certain key risks, akin to a mandated motor vehicle or travel insurance, would go a long way to ensure that impacted entities are in a position to pay out compensation for personal data that is lost.
Conclusion
Though India has been off late paying greater attention to cyber security, the rising number of attacks on India should be very worrying to Indian cyber security managers. The data above point that India is gradually drifting to become the epicenter of cyber pandemic. Whether these attacks lead to data or financial loss or not, the more serious issue is the ability of the perpetrators to crack the Indian cyber security system, despite India’s security efforts. They also reflect the still-inadequate protection measures afforded to critical information infrastructure in India. The government needs to step up its data protection efforts through additional measures if it is to prevent such frequent cyberattacks. The absence of awareness of cyber risks among the users and the use of old, legacy technologies are among the factors that add to the vulnerabilities. India also needs to study the evolving tactics, techniques, and procedures (TTPs) of hackers and criminals to be able to prevent these attacks. India will pay a serious price if it is seen as an easy target. Question remains – Is India sitting on the edge of the cyber pandemic?
![]()