
Iqbal Singh
Technology Expert & Senior Corporate Executive in a European MNC
Imagine you booting your laptop in the morning to start your workday and you have the below message staring at you from your laptop screen. This is an example of a screen-locking ransomware that holds your computer hostage by blocking your access to the operating system and there is almost nothing you can do to access your files and data on your laptop.
Now imagine the victim of ransomware instead of being a single user in an organization, maybe an oil pipeline company with a pipeline network of nearly 9000kms or a meat company with plants across the globe or a 800 store retail company. Yes, all of these are real examples of organizations who have been recent high profile victims of ransomware.

Ransomware is ravaging the world | Andrey Popov / Getty Images
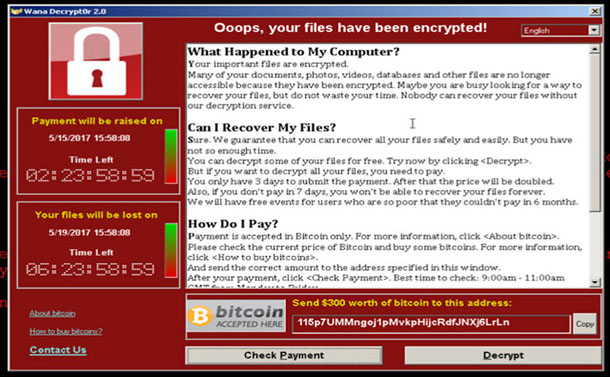
WannaCry ransomware note. Image: Cisco Talos
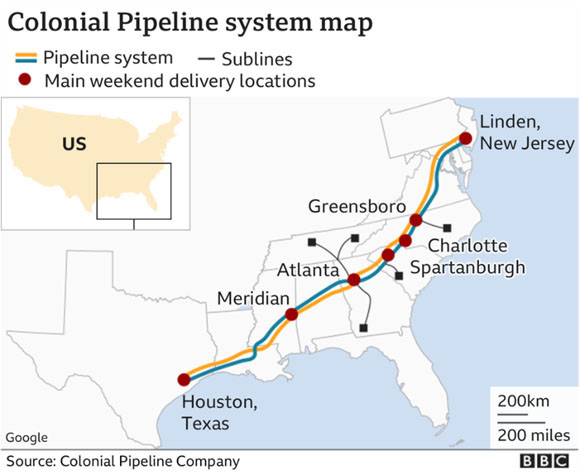
On 07 May 2021 an employee of Colonial Pipeline – the company with the largest pipeline in the USA found a ransom note from hackers on a control-room computer. This provoked a shutdown of their operations for five days, which resulted in a temporary fuel shortage along the East Coast, leading to spike in gas prices and huge queues of consumers at gas stations. The CEO of the company confirmed that they paid a ransom of $4.4 million.
30 May 2021 JBS, the largest beef supplier in the world, suffered a cyberattack, disabling its beef and pork slaughterhouses. The attack impacted facilities in the United States, Canada, and Australia. The company paid a ransom of $11m to the hackers.
The Swedish Coop grocery store chain closed all its 800 stores on 03 Jul 2021 after a ransomware attack on American IT provider Kaseya left it unable to operate its cash registers. Hundreds of American businesses were also hit by an unusually sophisticated attack that hijacked the widely used Kaseya software.
What is Ransomware?
Ransomware is a form of malicious software – malware – that encrypts files and documents on anything from a single PC all the way up to an entire network, including servers. The attacker then demands a ransom from the victim to restore access to the data upon payment. Victims can often be left with limited choices; they can either regain access to their encrypted network by paying a ransom to the criminals behind the ransomware or restore from backups or hope that there is a decryption key freely available. Or start again from scratch.
Hackers have been mostly unforgiving and ruthless in choosing their ransomware targets. They have not spared even health-care providers, municipalities and schools, big commercial organizations, of course, are expected tempting targets. The Washington Post found that ransomware attacks in the United States more than doubled from 2019 to 2020. One of the unfortunate success stories of the coronavirus times has been ransomware. Studies consistently show that the scale and cost of ransomware continues to grow.
Methods of Infection
Understanding how ransomware infects and spreads is the key to avoiding falling victim to an attack. Post-infection, ransomware can spread to other machines or encrypt network filers in the organization’s network. In some cases, it can spread across organizational boundaries to infect supply chains, customers and other organizations.
All of the following can be vectors of infection for ransomware attacks:
- Phishing.
- Compromised websites.
- Malvertising.
- Exploit kits.
- Downloads.
- Messaging applications.
- Brute force via RDP (remote desk protocol)
History of Ransomware
Even though ransomware is making headlines in recent years the scheme is not new. The idea of taking user files or computers hostage by encrypting files, hindering system access or other methods and then demanding a ransom to return them is a few decades old. In the late 1980s, criminals were already holding encrypted files hostage in exchange for cash sent via the postal service. One of the first ransomware attacks ever documented was the AIDS trojan (PC Cyborg Virus) that was released via floppy disk in 1989. Victims needed to send $189 to a P.O. box in Panama to restore access to their systems, even though it was a simple virus.
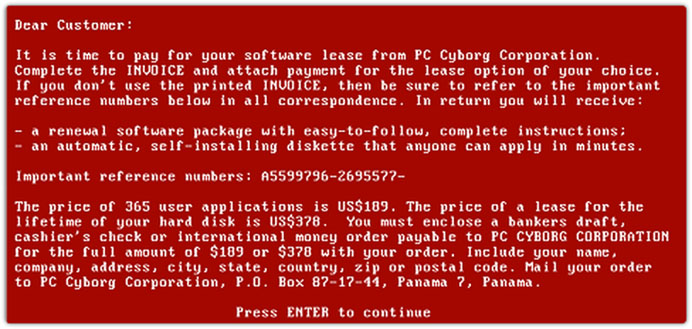
The AIDS demand for payment – by post. Image: Sophos
Ransomware attacks were still not that common well into the 2000s – probably due to difficulties with payment collection. It was the emergence of cryptocurrencies such as Bitcoin in 2010, that completely altered the landscape. It provided an easy and untraceable method for receiving payment from victims, virtual currencies created the opportunity for ransomware to become a lucrative business. Cyber criminals were quick to latch on to the monetization opportunity that Bitcoin created. This resulted in a substantial proliferation of ransomware beginning in 2012.
Intro of CryptoLockers
Ransomware was now moving from a petty crime into the realm of financial windfalls. Accordingly, the cyber criminals’ degree of technical sophistication also increased. The levels of encryption started improving from a 56 bit to 660-bit RSA public key encryption to 2048-bits RSA encryption keys by 2014. One significant development was the emergence of cryptolocking ransomware in 2013. CryptoLocker is a strain of ransomware so potent and dangerous that it took a dedicated global government task force to bring it down — but not before the cybercriminals behind it raked in millions of dollars from their hapless victims. It encrypts files on Windows computers, then demands a ransom payment in exchange for the decryption key. It first emerged in September 2013 in a sustained attack that lasted until May of the following year. CryptoLocker fooled targets into downloading malicious attachments sent via emails. Once opened, these Trojan horse attachments would execute the malware hidden in[1]side. Just to give you an idea of the impact CryptoLocker raked in a revenue of $30m within the first 100 days of its appearance. Earlier the encryptions used symmetric keys (same key to crypt as well as decrypt), however, CryptoLocker uses an asymmetric encryption method that makes it difficult to crack. This two-key system uses one public key for encryption and one private key for decryption, each linked to the other. When asymmetric encryption is used for legit purposes such as transmitting sensitive information, the receiver will give the public key to the sender so they can encrypt the data, but keep the private key to themselves. With ransomware like CryptoLocker the operators hold onto both keys, including the private key that you need to decrypt your files.
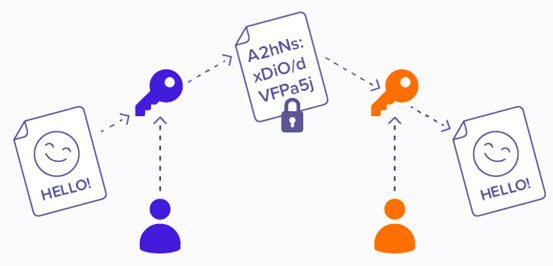
Asymmetric Encryption: The sender encrypts a file with the
public key, and the recipient decrypts it with their private key.
Source: Avast
JavaScript Ransomware Appears
In 2016 a new form of ransomware appeared, the malware would ride on Javascripts. JavaScript is one of the most common programming languages used in the development of websites. It is established that over 95% of all websites contain at least some JavaScript code. When browsing the internet, you’ll probably encounter JavaScript code. It allows for unique interactions between the website and your web browser, which otherwise wouldn’t be possible. When you visit a hijacked website that contains JavaScript code, you’ll download that code to your computer. Hackers add the malicious Javascript code to websites, thus infecting visitors with their malware.
Ransomware Hits Big Time Nation State Sponsored Ransomware
For tens of thousands of people in the UK, the first time they heard of ‘ransomware’ was as they were turned away from hospitals in May 2017. The WannaCry ransomware had shut down computers in more than 80 NHS ( National Health Service) organisations in England alone, resulting in almost 20,000 cancelled appointments, 600 GP surgeries having to return to pen and paper, and five hospitals simply diverting ambulances, unable to handle any more emergency cases. Till now ransomware was centrally controlled, attacked new victims through direct mail campaigns, tricked users into downloading it, or through botnets of computers infected with other malware– going in through the front door, so to speak, rather than using weaknesses in computer systems to spread.
WannaCry Changed That
WannaCry was the first ‘ransomworm’ the world had ever seen. A ‘worm,’ in computing parlance, is a piece of malware able to spread itself to be far more damaging than your typical computer virus by self-replicating themselves moving from host to host just like an epidemic grows exponentially. As computer security techniques had improved, worldwide worm outbreaks had become rare. It is hard to engineer a piece of malware that will automatically execute on a remote machine without any user involvement. Before WannaCry, the last major worm to hit the wild was Conficker. But since Conficker, major worms had been rare. In April 2017, a hacking group called The Shadow Brokers released details of a weakness (named EternalBlue) in Microsoft’s Windows operating systems that could be used to automatically run programs on other computers on the same network. Microsoft fixed the EternalBlue weakness in March 2017, before it was released in public, tipped off by the NSA (National Security Agency). But two months later, many organisations had yet to install the patch.

Marcus Hutchins, who stopped the WannaCry ransomware
attack from spreading. Photograph: Frank Augstein/ AP
WannaCry exploited this vulnerability. Since WannaCry was so damaging and spreading so fast that security researchers were tearing it apart within hours of it appearing in the wild. One of them British Marcus Hutchins discovered that affected computers tried to access a particular web address after the infection. Curiously, the address wasn’t registered to anyone, so Marcus bought the domain – and just like that, the malware stopped spreading. It’s still not clear as to why WannaCry included this kill switch. It was felt that WannaCry was a relatively unsophisticated attack and more sophisticated attacks could happen soon. Sure enough a month later another attack labelled NotPetya appeared. The malware was clearly built on the lessons of WannaCry, using the same EternalBlue weakness to spread within corporate networks, but without being able to jump from one network to another. NotPetya infected the victims through a hacked version of a major accounting program widely used in Ukraine. It still took out companies far and wide, from shipping firm Maersk to pharmaceutical company Merck – multinationals whose internal networks were large enough that the infection could travel quite far from Ukraine. NotPetya had something quite strange – it didn’t actually seem created to make money. The ‘ransomware’ was coded in such a way that even if users did pay up, their data could never be recovered. It was fair to conclude that if a nation state were to write malware with the aim of crippling the economy of its target then it would be very similar to NotPetya. This was a major shift, it seemed that not just petty cyber gangs but even nation states were getting into the game of ransomware.
Emergence of Big Game Hunting (BGH)
This is a new trend where cybercriminals are setting their sights on bigger prizes and we are seeing a shift towards what is known as Big Game Hunting TTPs (Tactics, Techniques and Procedures). Hackers are targeting bigger organizations and high profile individuals, in an attempt to steal high-value assets or data so they can hold the information at ransom. Unlike in the past where threat actors would try to compromise as many systems as possible, irrespective of who owned those systems and what data sat on it, Big Game Hunting uses an extremely targeted approach. The attackers will usually target organizations that are particularly sensitive to downtime, as it increases the motivation to pay the ransom. As a result, the industries typically targeted by these particular cybercriminals include local governments, academic institutions, the technology sector, healthcare, manufacturing and financial services. SolarWinds hacking fell in this category.
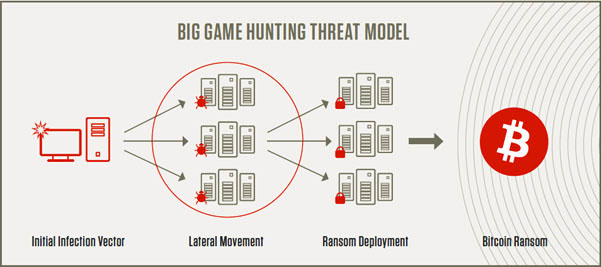
Typical Steps in Big Game Hunting Threat
Big Game Hunters identify and study specific targets and deploy sophisticated methods to install ransomware in their victims’ networks. As a result, groups can spend several months lurking in a victim’s network before deploying ransomware or stealing any data. One of the most common ways that these cybercriminals are gaining access is by exploiting the Remote Desktop Protocol (RDP) servers.
Another method of entering victims’ networks being used by these groups, is through known vulnerabilities in the software. Common vulnerabilities in the network could be in the form of outdated/ unpatched software that can be easily exploited by social engineering attacks and/ or malware.
Who are these Hunters? Some experts believe that organized gangs in Russia and Eastern Europe, or state-sponsored hackers are those responsible for launching these attacks. One particular group, ‘DarkSide’ claims to have already made ‘millions of dollars of profit’ from their ransomware endeavours. They exclusively target large profitable corporations. If the ransom isn’t paid then Darkside will leak the company’s data online, via the dark web.
Preventive Measures
The best way to get avoid getting sick is to stay healthy – this applies to ransomware as well.
- Regular Backups of Data. This will help restore the data in the least disruptive way possible with the most recent data available.
- Update the Software. The software and operating systems should be kept up to date with the latest security patches, to stop cyber criminals from exploiting known vulnerabilities to help carry out ransomware attacks.
- Multi Factor Authentication (MFA). Ensure that corporate networks and remote desktop protocol (RDP) services are secured with MFA to provide an extra barrier to help stop cyber criminals from being able to access the network in the first place.
- Watch Your Clicks. Educate your users not to open email attachments from unknown sources and visit insecure websites.
- Avoid Sharing Personal Details. Again, the users need to be sensitized to NOT share credentials over email/ phone to avoid phishing attacks.
- Software Downloads. Software updation must only be done from official websites of the OEMs.
- Privilege Account Management. These accounts should be given only on a need basis and just-intime access is recommended. These accounts must also be monitored regularly to review their continuation.
- Network Segmentation. This approach that divides a network into multiple segments or subnets, each acting as its own small network. This allows network administrators to control the flow of traffic between subnets based on granular policies. Organizations use segmentation to improve monitoring, boost performance, localize technical issues and – most importantly – enhance security.
- Compartmentalize Sensitive Data. In our digital lives ‘don’t put all your eggs in one basket’ is really talking about compartmentalization – categorizing and separating our private data into many different compartments to reduce the impact when it is compromised.
- Monitor Data Exfiltration. Ensure that you are monitoring data exfiltrating out of your network. Data exfiltration occurs in two ways, through outsider attacks and via insider threats. Both are major risks, and organizations must ensure their data is protected by detecting and preventing data exfiltration at all times. This is how the SolarWinds hack was discovered in Dec 2020 by FireEye when they discovered data exfiltration happening from their network.
- Penetrate Testing of Your Systems. A penetration test is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behaviour. Such assessments are also useful in validating the efficacy of defensive mechanisms, as well as end-user adherence to security policies.
- Cyber Liability Insurance. This is a necessary protection in the present day and age.
How to Respond to a Ransomware Attack
The first step is to isolate the affected systems from the network. The last thing we need is the infection spreading to other systems. The second step is to figure out as to how did the malware get in. The third step is to make sure that your backups are secure. And it’s absolutely essential to note that you don’t access those backup servers using any of the already compromised infrastructure, the reason being that sometimes ransomware still running on them.
How organizations proceed from here depends upon whether they have working backups or not. If they do not have working backups and the victim decides to pursue paying a ransom (which is not ideally recommended) they should use a professional negotiating service. These firms have knowledge of individual ransomware operations, including typical ransom pricing and whether they tend to provide a decryptor or not as they are in this game day in and day out. There are also cases where ransoms were paid, even though it wasn’t necessary – this possibility can be obviated using this professional advice. It is also advisable that the victim reaches out to security companies, orgs for free advice on any other approaches that might be available for recovering data. Also reach out to the law enforcement agency in your country e.g., ICO in UK, FBI, CISA in USA, or whatever the data protection organization is in your particular country.
Free Decyrptors: Some govt or non-profit orgs also offer free decryptors like the No More Ransom Project – https://www.nomoreransom.org/en/index.html. The project, founded by Europol, the National High Tech Crime Unit of the Netherlands’ police, Europol’s European Cybercrime Centre, Kaspersky, and McAfee, launched in 2016 and has grown to involve 170 partners across law enforcement, cybersecurity companies, academia, and others. They currently provide 121 free ransomware decryption tools which can decrypt 151 ransomware families. They’ve helped more than six million ransomware victims recover their encrypted files for free – all without the need to give into the demands of cyber extortionists.
Conclusion
Ransomware has certainly become a lucrative business and it is likely to continue growing. However you can ill afford to let the risk or cost of ransomware storm your organization’s castle. It can be a havoc not only to your data but also to your business continuity. While there is no single silver bullet against ransomware it is important that you invest in your security, train your employees and stay updated with the latest threats in the cyber universe as also explore cyber insurance. Remember minimizing the risk is cheaper than restoring the business disruption.