
The primary objective for smart city initiatives is to intelligently use data and technology to make everyday life easier and better for the people who live in, work in and visit the city – while making innovative and efficient use of resources. Public safety plays an important role. This is why most smart city initiatives include video surveillance for key public areas, to achieve quicker alerting and better data to inform first responders regarding accidents, crimes and public safety situations.
However, if smart city initiatives take traditional approaches for physical security technology, they will undermine their primary smart city objective. Over a decade of smart city initiatives has revealed what it takes for smart city technology deployments to achieve the sustainable quality of life transformations they intend, in the face of the challenges that smart city tech projects face.
Recent successes have shown that cloud-based solutions are indispensable elements of smart city infrastructure, which includes both public and private infrastructure elements. Cloud-based deployments are essential for cost-effectiveness, scalability, and short deployment time frames. Furthermore, smart city security technology projects have new technical requirements – some of which can only be met using cloud technology. This paper examines those requirements and points to two very recent projects that exemplify the kinds of success that can be achieved.
Smart Cities
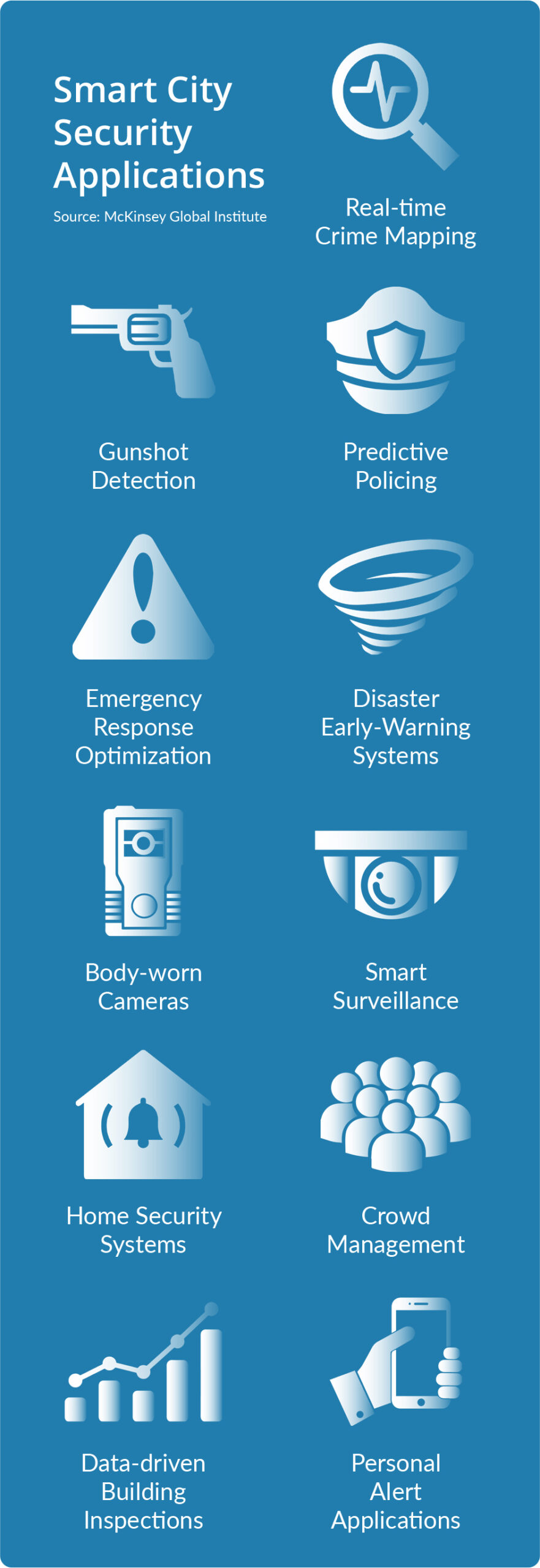
In June 2018, the McKinsey Global Institute released an in-depth independent research and analysis report titled, ‘Smart cities: Digital solutions for a more livable future.’ McKinsey’s research identified 60 data-driven smart city applications spanning the eight domains listed below. Eleven of these applications are physical security applications.
Smart Applications
Successful smart city security initiatives require more than just getting city planners and stakeholders, and their security integrators and consultants, on the ‘same page.’
They must all get on a ‘new page’ that includes:
- Expanded system design thinking.
- Up to date set of technology capabilities.
- Active stakeholder and citizen involvement.
All are required for smart city deployment success.
The Smart City Context
The requirements for security technology deployments derive from the ways that smart city deployments differ from traditional security system deployments. The intelligence and operational capabilities of smart cities technology infrastructure resides in three layers identified by McKinsey analysis – technology base, applications interaction, and user base. This is the context for smart city security tech deployments.
Technology Base
Smart city security devices and systems are part of a larger city technology base connected by reliable high-speed communications networks. Achieving reliable high-speed internet access is always the first step in smart city development – unless it already exists.
Applications Interact
Applications are the tools by which a smart city turns raw data into alerts, insights and action – automating as much of the job as possible. Smart city security application design must consider that application data should not just facilitate public safety operations but must also contribute to the city’s greater understanding of itself. This is plain to see in Mexico City’s recent smart city security initiative.
Public Usage
The size of a smart city’s user base is the most significant difference from traditional security systems, which typically range from a few dozen to a few hundred users. Smart city citizen apps include personal security and safety features and have many thousands to millions of users. These mobile apps are the way smart cities enable citizens and visitors to interact with city services, including real-time services such as parking, public transportation, security and emergency services. This is an area where security technology and service providers can be innovative in providing value for citizen end-users as well as for city operations.
Key Technology Requirements
Smart city technology initiatives include 11 key requirements that have been traditional weak areas for physical security technology deployments:
- Intelligent connectivity.
- Simple scalability.
- Device and system interoperability.
- Open systems architecture.
- Systems integration interfaces.
- Privacy.
- Cybersecurity
- Data governance.
- Actionable data and analytics.
- Fault-tolerance.
- Future-readiness.
The security industry has begun improving in some of these areas. However, physical security technology has typically lagged five to 10 years behind the state of information technology and related IT practices, and exponential technology advancement has made catching up an even greater challenge.
Modern Technology is Required
For large-scale smart city projects it’s not possible, for both technical and cost reasons, to adequately address most or all these 11 requirements with traditional on-premises devices and systems. However, well-engineered cloudbased systems with cloud-managed field devices make it both technically possible and financially feasible to fulfill smart city key requirements. These key requirements are well understood in the IT industry, but only recently has physical security technology advanced to the point where meeting all of them is feasible in smartcity security deployments.
Intelligent Connectivity
Smart city networks are, for the most part, very large shared networks – both wired and wireless. That means devices and applications that use significant bandwidth – such as security video – must not only use data stream reduction techniques such as compression and recording on motion and alarm, they must also be aware of LAN and internet bandwidth availability, and intelligently buffer transmissions as needed to throttle back their usage during times of peak overall network utilization.
Develop a sound networking plan for any proposed project, verifying the infrastructure capabilities and documenting the planned intelligent use of existing network infrastructure and any new infrastructure to be added.
Simple Scalability
On-premises systems have fixed capacities for compute, memory, disk storage and networking. Well-engineered true cloud systems can scale those resources up or down on demand. NIST defines cloud computing as “a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (for example, networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
A true cloud application – not just a client-server system hosted in the cloud – supports cloud-managed local devices and maximally automates their management. Automation includes performing system-wide firmware upgrades and digital certificate issuance. Well-designed cloud-based systems and tools can enable large-scale parallel device updates on a zoned or system-wide basis, because their ability to interact with a very high number of devices at once is not constrained by fixed resources.
Explore the future vision of the smart city infrastructure and document how the modern solution being proposed will satisfy current needs and also be both expandable and manageable for future growth.
Device and System Interoperability
The fact that physical security industry systems and devices are built using information technology has resulted in standards-based interoperability at many levels. For example, Microsoft® Active Directory® integrations for security software applications are now commonplace. Leading cameras and other devices support 802.1x authentication, digital-certificate-based encryption, device and computer time synchronization via Network Time Protocol (NTP), and device and computer monitoring via Simple Network Management Protocol (SNMP).
However, many security products don’t use the current versions of the protocols and thus don’t fully qualify themselves to be part of a smart city’s technology base infrastructure. A multiplicity of protocol versions needlessly complicates configuration of cybersecurity and network management features.
On the other hand, many manufacturers are willing to update their products to bring them current for smart city projects, meaning that design engineers and consultants must play close attention to the protocol and interoperability requirements of smart city initiatives.
Ensure that the immediate interoperability requirements have all been identified. Work out and document how they will be addressed by current product capabilities or near-term vendor roadmap items.
Open Systems Architecture
An architecture identifies components, the relationship between components, and the rules for the architecture’s composition. An open system uses well defined, widely used, non-proprietary, or openly-published interfaces and protocols, as well as industry standards, to facilitate interoperation with other components on local and remote open systems, and to facilitate the development and use of user interfaces based on specific user roles and their tasks.
The term open systems architecture describes an approach to designing systems and their means of interacting that is necessary to support the kind of intelligent functionality and data utilization from which growing smart city systems are built.
The scope of a smart city’s intelligent infrastructure is intentionally not fixed, but expands in micro and macro ways as the city grows in size, capability, and sustainability, and as the technologies it embraces advance exponentially.
For more information about the smart city need for extensibility in product offerings and for thinking strategically beyond point solutions, see the recent Gartner report, ‘Emerging Technologies: Top Use Cases for Future-State Physical Security Infrastructure.’
Don’t just conform to smart city planning, but contribute to it – especially for strategic infrastructure design and elevating the citizen and visitor experiences.
Data Governance
Data governance refers to the people, processes and technology used to manage and make proper use of an organization’s data, whether internal or external to the organization. Smart cities value the activity and person information generated by physical security systems, and require the origination, secure processing and use of such information to be fully-documented and performed in accordance with city data governance requirements.
Fully understand the smart city data governance plan, and the directions in which it is evolving. Provide a privacy, cybersecurity, and data governance plan for the security technology deployment that shows how the city’s requirements will be met or exceeded.
Actionable Data and Analytics
Machine-learning based analytics are advancing exponentially, improving the performance of intelligent devices and systems used to provide actionable insight for city operations, including security operations. Additionally, video-based analytics have proven to be of tremendous value to retail stores, that use them to gain deep insights into their effectiveness of store layouts, displays, and sales campaigns.
A smart city will include opportunities like these:
For example, the experience accessing residential and business parking spaces across Switzerland, Austria and Germany recently was enhanced by Eagle Eye Networks, Brivo, and any2any, the digital experience platform creating secure connected experiences. The any2any clients can not only find and pay for parking by phone in the downtown core of selected cities, they can also easily access the parking spaces via license plate recognition offered by Eagle Eye Networks and Brivo. Such projects require little initial infrastructure investment, as the core functionality is provided via the cloud applications, which are available via annual subscription.
Also see the Gartner report for a description of the key role of video analytics as a driver for new and upgraded security operations centers, as well as smart city security technology deployments.
Security technology service providers should consider the many opportunities that are appropriate for a city seeking to improve the smart city venue experiences.
Fault-Tolerance
Smart cities expect their security applications to be fully functioning and accessible 24/7. A true cloud application that offers the kind of compute, data storage, and networking redundancy as well as computing fault-tolerance best suited for a city’s emergency response capabilities. Equivalent levels of fault-tolerance are generally not cost-feasible in fully on-premises systems. The section that follows below titled, Smart City Engineering, provides examples of highly redundant system components.
Be sure to engineer end-to-end fault-tolerance in smart city technology deployments. Also, be sure to specify fault-tolerance as a requirement for any data sources or systems integrations that your technology deployment will depend on for real-time operations.
Future-Readiness
Future-readiness is achieved through the 10 key requirements above and the product and system capabilities that fully support them, plus manufacturer commitment to continuous product advancement and dedication to maximizing product and service value to customers.
Future-readiness includes engineering the means for current deployments to accommodate planned and likely future integrations with, support for, or provision of smart city infrastructure expansion and advanced application capabilities.
Smart City Engineer
For the Mexico City security initiative called MyStreet (MiCalle), the city turned to Omnicloud, a Mexican company specializing in cloud deployments, headed by CEO Jaime Abad Valdenebro. The company developed its own SaaS-based PSIM called OmniView and integrated it with the cloud-based Eagle Eye video platform, enabling the immediate deployment of more than 13,000 cloud-connected cameras from Eagle Eye Networks. The city’s command center is nicknamed ‘C5,’ which stands for command, control, computers, communications, and citizen contact.
OmniView provides the city’s C5 police emergency response user interface, including the video management system video user functionality. For the recent My Street initiative and to support potential future city initiatives, Eagle Eye provided critical functionality, described below, some of which were technology improvements added for use in the city’s deployment, all of which are applicable to any large smart city or enterprise camera deployment.
Eagle Eye MobileCam
Eagle Eye MobileCam is a versatile camera that connects directly via 4G/ LTE to the Eagle Eye Cloud Data Center, allowing users to view their video anytime and anywhere. The device is weatherproof and mobile, so it can be used almost anywhere. It captures video footage at 1080p and has a 138° wide-angle lens. It was formerly known as Panasonic Nubo or Eagle Eye NuboCam.
Eagle Eye Persistent Camera
Eagle Eye has patent-pending technology (US 16214246) embedded into Eagle Eye Connect that enhances the uptime video surveillance cameras. The technology allows a camera to analyze its own cloud connectivity status and take appropriate actions to recover if needed. For a smart city, this means less camera down time, fewer cameras down, and less maintenance. Intelligence has been added to the cameras to tune and control their bitrates automatically in cases of low latency or low bandwidth, which happens occasionally in 4G networks.
Eagle Eye Big Data Framework
The Eagle Eye Big Data framework consists of timebased data structures used for indexing, searching, retrieval, and analysis of video. These big data structures allow high performance efficient search and retrieval in large video data sets. Event data and analytics results can be attached to the video.
Eagle Eye Cloud Camera Specification
This specification is Eagle Eye Networks open standard for cameras to communicate securely with the Eagle Eye Cloud Data Center. Cameras that meet the specification will operate plug-and-play with the Eagle Eye Cloud VMS and Eagle Eye CameraManager. Eagle Eye provides certification and testing tools for the specification.
Eagle Eye Cloud Mobile/ Body Camera Specification
This specification is the Eagle Eye Networks open standard for mobile/ body cameras to communicate securely with the Eagle Eye Cloud Data Center. Cameras that meet the specification will operate plug-and-play with the Eagle Eye Cloud VMS and Eagle Eye CameraManager. Eagle Eye provides certification and testing tools for the specification.
Eagle Eye Device Compatibility Test Tool
This Eagle Eye application may be used by manufacturers to verify their camera meets the requirements defined in the Eagle Eye Cloud camera specifications.
Eagle Eye Connect
Eagle Eye Connect is a technology (a communications protocol and the POSIX-compatible Linux code that implements the protocol) by which cameras automatically connect for encrypted, secure, and reliable communications to an Eagle Eye Cloud Data Center. For My Street, Eagle Eye added camera-based edge storage to cover potential 4G outages, including automatic sync-back of video to the cloud.
Currently Eagle Eye Connect is being expanded further to support NVRs and DVRs for specific use cases, to provide a flexible option for monitoring centers to use large on-premises video storage devices in a secure and reliable way.
Eagle Eye Cloud Device SDK
This Eagle Eye Networks Linux-based SDK is made available to camera/ NVR/ DVR manufacturers at no charge, to speed their development of devices that meet any of the Eagle Eye Cloud specifications. It implements the Eagle Eye Cloud Connect protocol in a small library.
To support future My Street capabilities, the Eagle Eye Cloud Device SDK was given support for Android OS that allows third parties to embed Eagle Eye Connect in Android-based surveillance cameras such as smartphones and body-worn cameras. A smart city can use this technology to allow citizens or professional security officers to stream live video to a monitoring center to give the city more ‘eyes’ during critical situations. For example, taxi drivers who cannot afford a mobile video kit that connects to the C5 center, can simply use a smartphone to summon help from C5 and stream smartphone video to the center.
API Enhancements
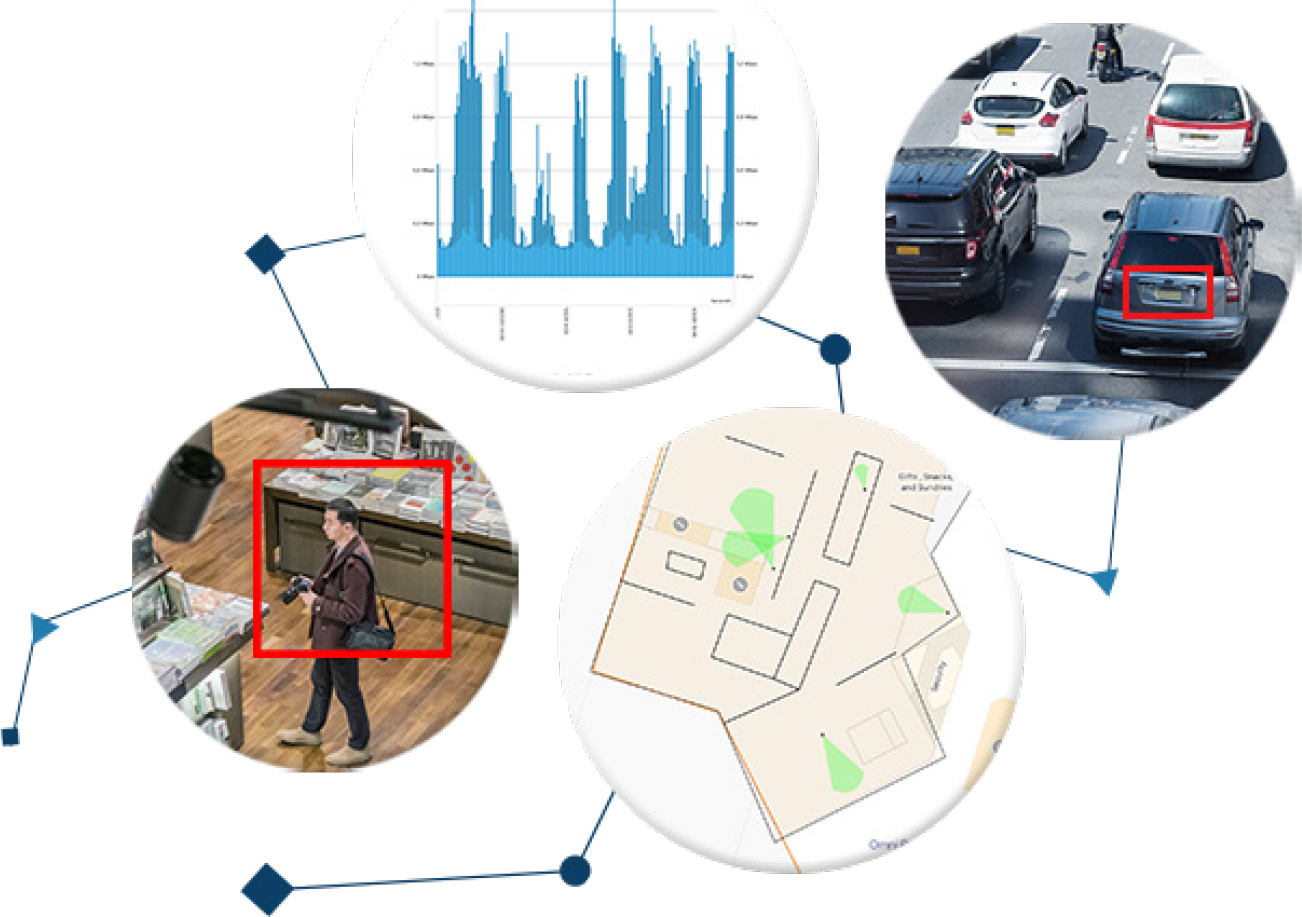
The open, restful Eagle Eye Cloud Video API is designed so customers who have extensive data in the Eagle Eye Cloud Data Center can build innovative services for processing their information using the application processing interface. Such services include behavioral analysis – live and forensic; license plate read; vehicle make, model, and color for forensics; face recognition; skin temperature monitoring; speech analysis; nonvideo sensor data/ video correlations; and others.
OmniCloud has used the Eagle Eye Cloud Video API to turn its OmniView PSIM into a full solution for the My Street project. During this process, Eagle Eye identified unique opportunities to enhance the cloud API with functionality critical to a smart city. One example is the API for on-demand synchronization of video recorded on the device edge to the cloud to make it available for playback by the monitoring center in a matter of seconds. Through this enhancement, not all video has to be cloud-recorded to be viewable, which allows video buffering to optimize the use of the smart city 4G network without impacting user viewing capabilities.
Smart City Security Architecture
The example system architectures for several Mexico City current and potential future security applications are provided below. The OmniView application is a fully secure cloud security services platform integrated with the C5 alarm reception and monitoring systems. Under this configuration, direct and immediate communication with the C5 operators is enabled via panic button, both physical and virtual (smartphone app). Likewise, system cameras positioned in business and residence locations may be monitored by business personnel and residents through OmniView mobile apps.
Business Security
Figure 1 shows an architecture for a variety of businesses, including financial institutions.
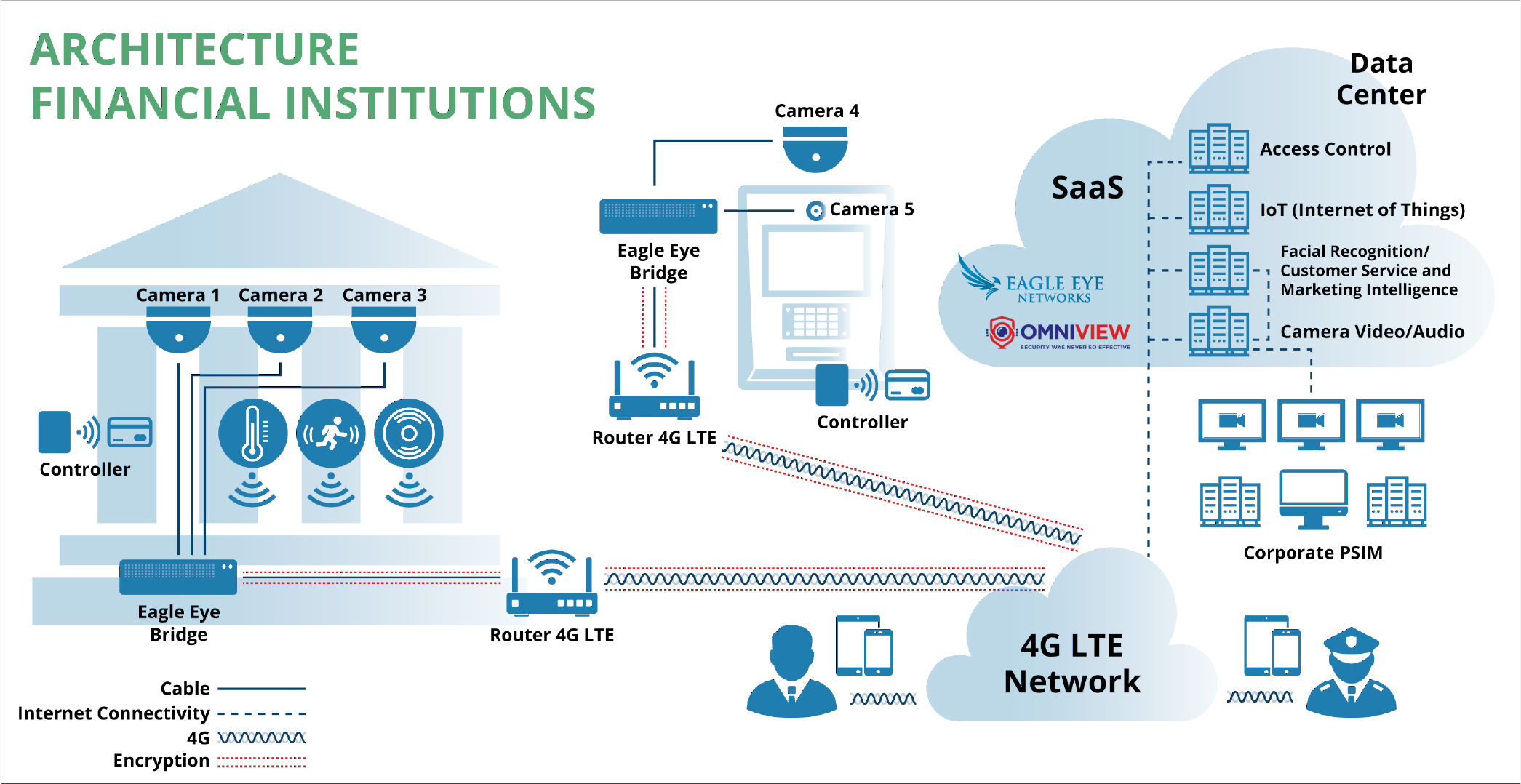
Smart Retail features of this application provide real-time operational data for high-performance customer service management, and marketing intelligence that ties actual results back to marketing campaigns.
This architecture supports any number of cameras on site. Its advantages include:
- No dependency on fault-sensitive items, such as onsite DVRs, NVRs and servers .
- Greater ease of management in large deployments.
- Triple redundancy of cloud data centers.
- Availability of recordings and access to service greater than 99.99 percent.
- Unlimited number of users can simultaneously access the same cameras.
Citizen Safety
Figure 2 illustrates an architecture applicable to public street areas, small businesses, and residential dwellings.
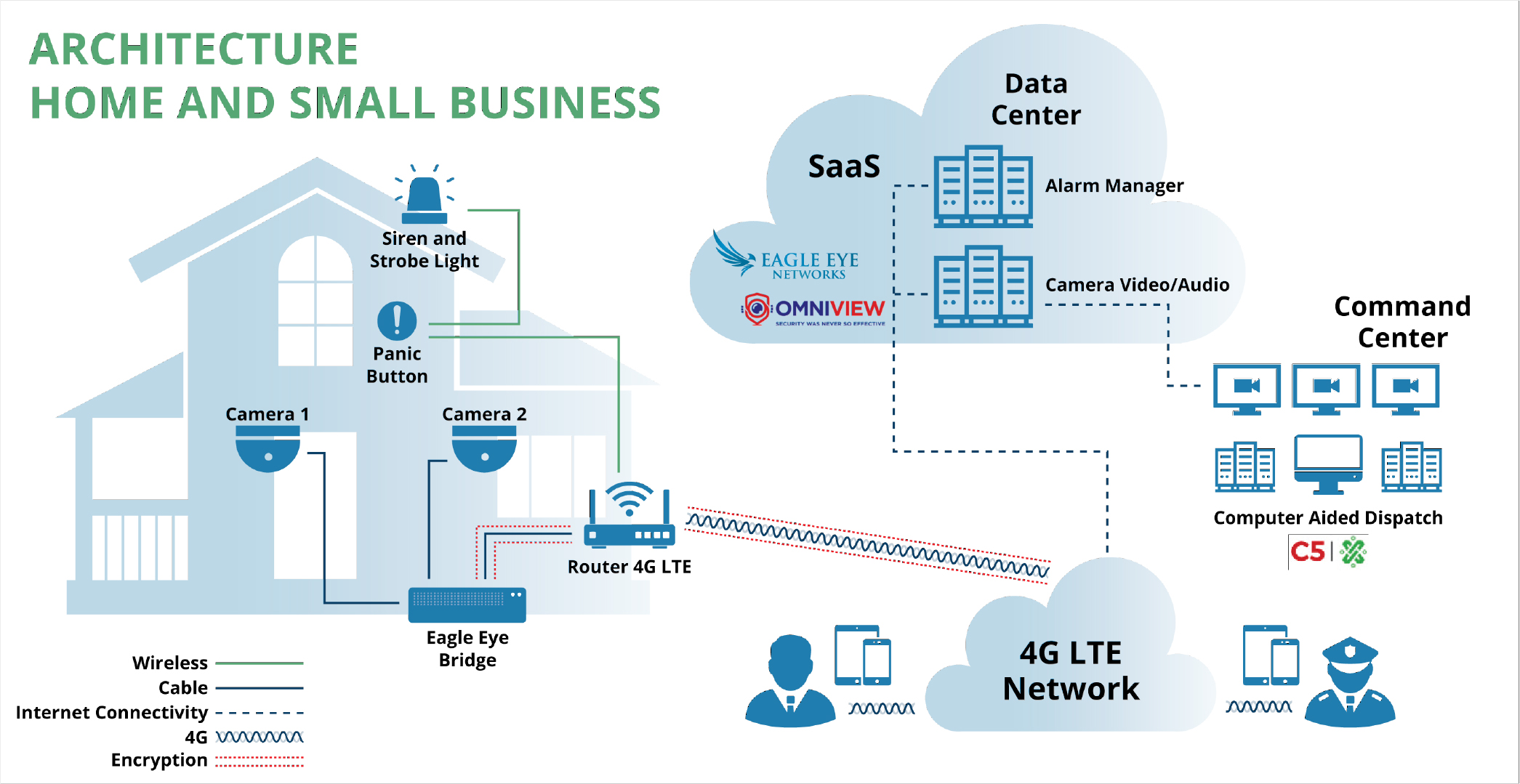
This configuration provides direct communication by physical and virtual panic buttons with C5 operators for immediate police and emergency services response. Business and residence occupants access the video and virtual panic button features via smartphone app. It supports any number of cameras on site, which typically number two to six.
Public Safety Operations and Policing
Cloud-based solutions enable faster, more-informed response with greater situational awareness. Figure 3 illustrates architecture appropriate for police vehicles and their officers.
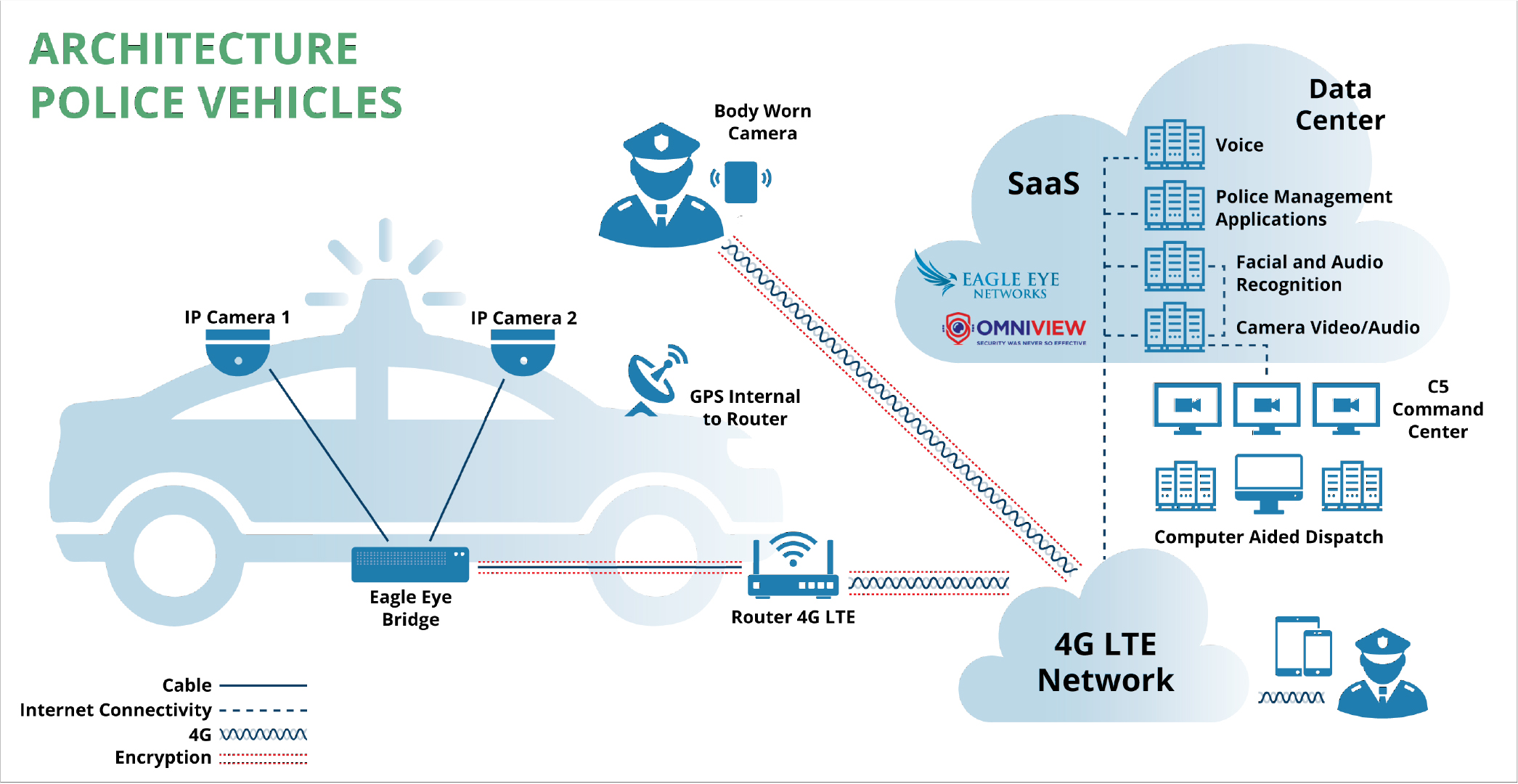
These capabilities are implemented by the architecture above:
- Constant communication between body-worn cameras and the OmniView platform, as well as between police vehicles and OmniView, uses flat rate wireless LTE broadband service for transmission of the video, and audio-signals the cameras to a Control Center and Data Center for live monitoring and storage available at all times.
- In case of signal loss, all video sequences are stored in the camera’s local SD memory card or in the Camera Bridge, as appropriate. After communication is re-established, cameras initiate synchronization of all cloud-stored footage, along with the current video, to ensure the integrity of the video and audio streams OmniView.
- There is no limit to the number of users who can simultaneously view live and recorded video. The My Street project users include C5 center operators, the closest police station, the police patrol closest to the event, directors of C5 operations, etc.
- Cloud-based video analytics provides facial recognition for the body-worn cameras, both for real-time applications and forensic tasks.
- The architecture enables integration of technologies from different providers, so there is no dependency on a single technology provider.
Public Transportation
In addition to public safety features, public transportation applications include monitoring and recording of data from the vehicle’s onboard diagnostics (OBD) system, allowing rapid remote identification of pending vehicle malfunctions and effective preventive maintenance planning.
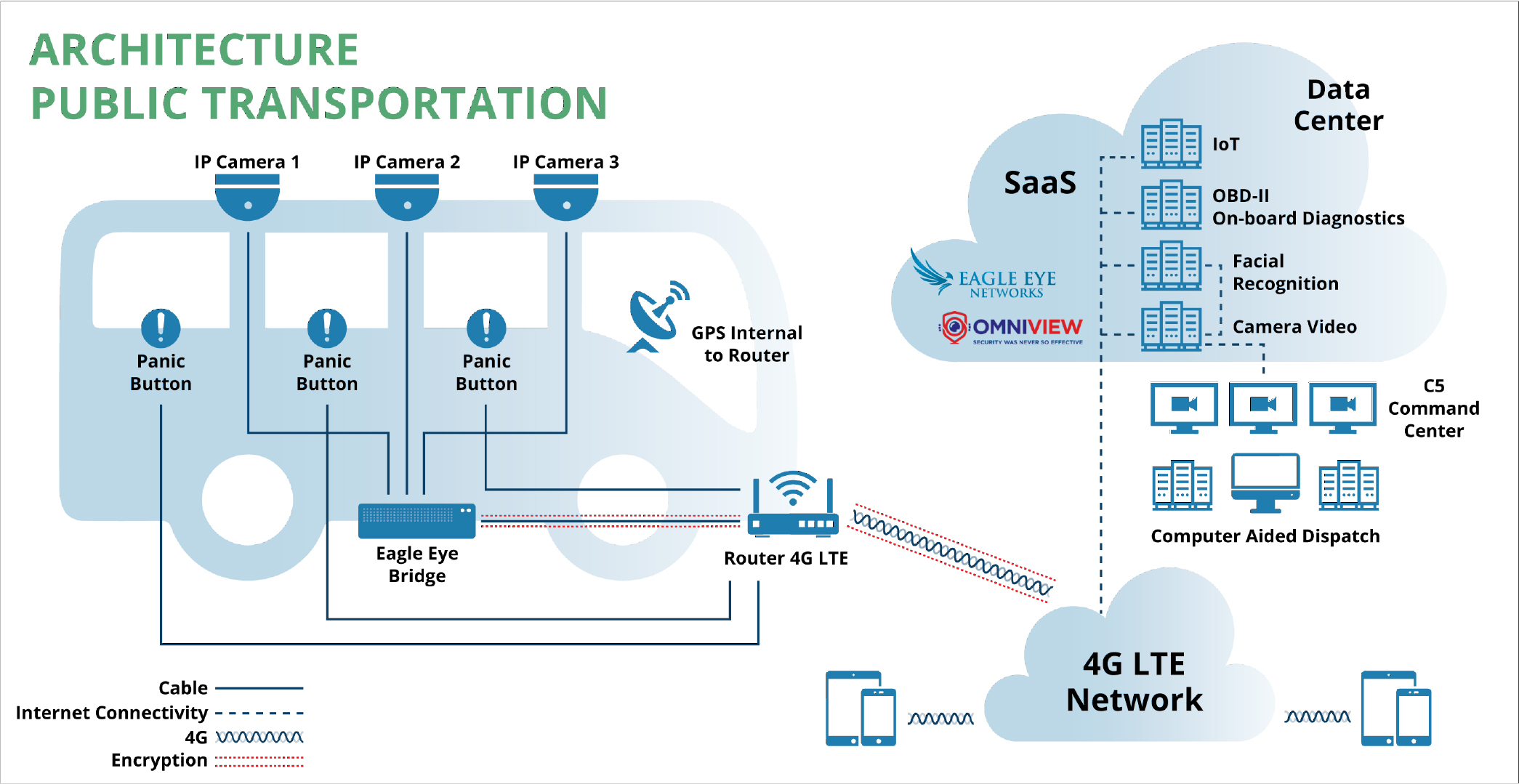
Mexico City plans, through the use of its MyStreet mobile app, to allow taxis and private ride service companies to use a smartphone as an in-vehicle camera, and also allow passengers to use the MyStreet app for duress or medical incident notification to C5 centers. Smartphone GPS data helps emergency responders locate the vehicle in real time, enabling effective response.
Technical Capabilities of Mexico City’s MyStreet Video Deploymen
The architectures described in the previous section enable the following technical capabilities for the city.
Cybersecurity
Strong standards-based cybersecurity is built into the cloud-managed on-premise devices as well as the datacenters and video management applications, including:
- Integrated firewall and routing functionalities.
- Total management of the bandwidth utilization.
- Automated Bridge/ cloud synchronization in case of connection loss.
- Device auto-discovery.
- Integrated video analytics.
- Video storage policies from 14 days to five years.
Cloud IoT with Wireless Sensors
- BLE or RF wireless communication.
- Automated Bridge/ cloud synchronization in case of connection loss.
- Wide variety of sensors.
Cloud Facial Recognition with Service and Marketing Intelligence
- High reliability in identification processes, even in outdoor environments.
- Biometric pattern metadata – face, gender, age, degree of satisfaction
- Analysis of visit frequency and stay times.
- Customer traffic and sales pattern analysis.
Broad Integration Capability
Open API-based integration capability for:
- Computer aided dispatch systems (CAD).
- Other PSIM systems.
- Fleet management systems (such as for GPS correlation.
