
Alexey Parfentiev, Senior Business Analyst, SearchInform
The biggest part of data leaks, which have ever been reported in various mass media sources, happened because of affected organizations employees’ fault. Some of them simply made a mistake, some of them acted deliberately. Let’s find out, what is an insider related risk, what factors cause internal data leaks and how to protect company against them.
Who are insiders and how they may affect an organization?
When it comes to data leaks, financial organizations are among most vulnerable ones. Despite they are usually protected way better than other companies, still, they always remain the focus of both general public and intruders’ attention. News on the leaks, containing thousands and millions of strings, are published regularly. For instance, Spanish branch’s databases of Zurich insurance company were exposed. They contained 4 million strings of data, retrieved from clients’ insurance policies. Such kinds of data leaks usually occur, because employees forget, that a cybercriminal isn’t necessary a mysterious hacker. Instead, any staff member may turn out to be an intruder. An insider is an employee of any organization, who has an access to confidential data. Confidential data include trade secrets, clients’ and employees’ personal data, payment details, intellectual property. Leaks of such data may result into reputational and financial loses, legal claims. According to SearchInform research, most commonly the following groups of specialists turn out to be culprits of data leaks: client managers (41%), supply managers (20%), accountants and financial officers (22%). Most vulnerable links of an organization are the departments, which employees deal with finance and critical data. Due to the peculiarities of the sphere, in financial industry just about every kind of information is critical and practically each employee is a potential insider.
Unintended violations
Not all data leaks happen because of malicious actions. Vice versa, usually they occur due to employee’s negligence or lack of knowledge in the sphere of information security. What’s more, they often happen accidentally. For instance, because of one insurance company’s employees’ negligence, copies of valid passports, drivers licenses, handwritten statements and some other documents were thrown away at the dump. All the documents weren’t disposed appropriately. Thus, unscrupulous employees threw away copies of valid documents, and didn’t even bother to burn or to shred them. In case this data had been obtained by intruders, document owners would have become victims of social engineering attacks. Also, there was a chance, that intruders could apply for a microloan using victims’ credentials. The most common mistake, which causes unintended data leaks is data access misconfiguration. For example, due to such misconfiguration, excel tables, containing lists of clients and information about their vehicles, were accessible on the website of one insurance company. It was possible to get access to the tables by inputting any client’s surname on the web site.
Another attack vector is phishing or BEC-attack, which may also result into accidental leak of critical data.
Phishing is a type of fraud, which main aim is to steal confidential info or to force victim to commit some undesirable actions. To achieve the goals, intruders treat victim in order to gain his or her trust. Usually, this type of attack requires usage of the following instruments: email, fake web sources, phone calls and SMS.
BEC-attack Corporate e-correspondence compromising, in particular, with the help of phishing.
Occasionally, such attack is divided into a few stages. With the help of phishing cybercriminals manage to obtain account data of a staff member, in order to reach out his or her boss later. Most frequently, attackers are driven by financial interest. However, sometimes they search for confidential data, such as client database or know-how documents.
Deliberate leaks
Such actions may be caused by plenty of different motives. For instance, insiders steal data in order to gain financial benefit, in such case they sell data to competitors or publish it on the darknet. Employees may be offended because of dismissal or deprivation of the bonus. In revenge, they leak data, revealing some information about the organization. What’s more, an insider can make a copy of data (for instance, copy it on a flash drive or upload to a cloud storage and use later, when he or she will change the company). This risk poses a threat not only to big corporations. Small and middle size companies are equally endangered.
Case study
An employee of our client, which is a reseller company, decided to resign after her request for promotion was denied. But before she quitted, the woman had uploaded a 900 megabytes archive to a cloud. This archive contained all company’s research data on the local market. The estimated price of the research was US$1,670,000. InfoSec officers prevented the data leak just in time and by the way revealed a fact of falsification of accounting documents.
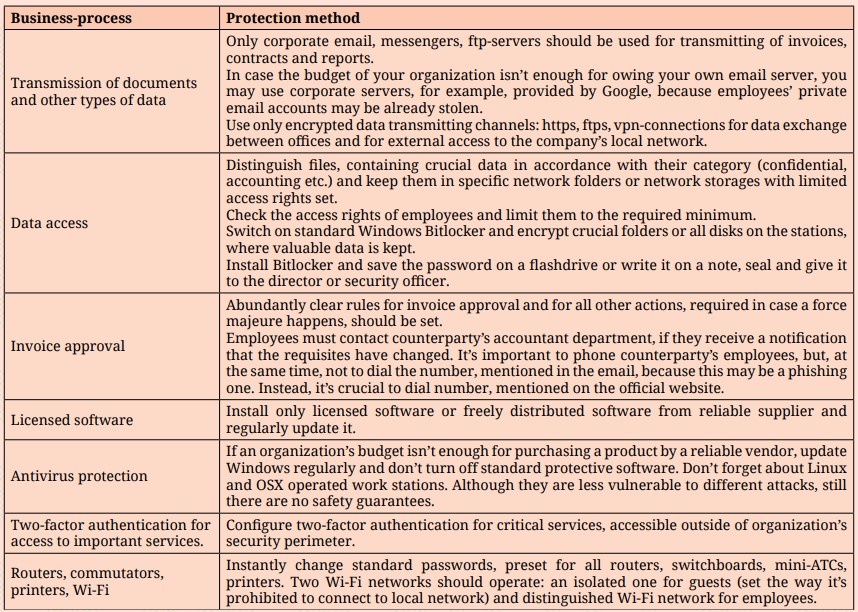
How to protect data against a leak
In fact, it’s possible to prevent insiders’ violations, but it’s crucial to understand and follow security regulations. First of all, this task refers to InfoSec and IT-department staff. Other department employees should understand that security requirements, set in an organization, are reasonable. Thus, staff mustn’t neglect the rules. That’s why it’s important to implement organizational measures, aimed at increasing the level of employees’ computer literacy. Full list of measures depends on the specific business-process. However, there are some basic rules.
Provide your employees with an educational course on the information security rules
The most effective way to prevent accidental leaks is to be critical when dealing with data. So, clarify this idea to your employees.
Tell your employees, which kinds of links they mustn’t open and in when it’s better to stop messaging with the email sender immediately.
Explicate, what is phishing
Tell your staff members, how do intruders use data about the recipient, pretending to be a counterparty in order to gain trust. Set the policy of reliable passwords in your organization. Explain employees, why is it crucial to lock the PC, when they leave their workplace.
It’s a good idea to make commemorative leaflets with illustrative examples. For example, our employees have created a document called ‘Pies with information security topping’, In this document we presented information about serious IS incidents in a poetic and ironic manner.
Occasionally evaluate employee’s knowledge
Send a fake email newsletter and monitor, who follows the recommendations on information security and who neglects them, opens the email, clicks on the link and downloads attachments. You can also do such checks without any conspiracy with the help of specific tests. They may be not too complicated and there is no need to assess employees and give marks for their tests. The aim is to help an employee to identify his or her ‘weak spots.’
Instruct employees how to identify, if an email sender isn’t an intruder and whom to call for verification. Make leaflets with official managers,’ strategic partners,’ clients’ and regulators’ emails and provide employees with links to their official websites. Thus staff members will be able to detect a camouflaged phishing letter or a link, leading to a fake page.
Both methods of employees’ self-education and usage of simple software in dealing with accidental insider leaks can be quite efficient. Nevertheless, even the most acknowledged and responsible employee can make a mistake in case of being overloaded. Although the willing to avoid extra expenditures is sensible and understandable, it’s important to keep in mind, that security always costs a fortune, but, definitely, it worth it. The most effective way to ensure corporate safety is to employ an information security officer and to implement an effective system of control. Specific software, DLP systems, help to prevent data leaks and to investigate various information security incidents. In case organization’s staff number is less than 100 people, it’s sensible to choose MSSP, as it helps to reduce costs.
![]()