
Garima Goswamy, Associate Protection Professional,
Chief Executive Officer and Co-Founder, Dridhg Security International Pvt. Ltd.
OSINT or Open-Source Intelligence is nothing new. It is information gathering from publicly available sources, which are out there for everyone to see. It has been used extensively by investigators – private and public across generations in their assignments and missions. In fact, during the second world War, Lt. Gen. Samuel V Wilson, who headed the American Defense Intelligence, made an astounding claim – he received 90% of intelligence through open sources. Today in 2023, with a variety of sources available, especially with possible access to the deep web, dark web and regular search engines, and a multitude of social media platform, it becomes exceedingly difficult to retrieve useful information – unless one is adequately trained in usage of OSINT or familiar with different OSINT tools and techniques.
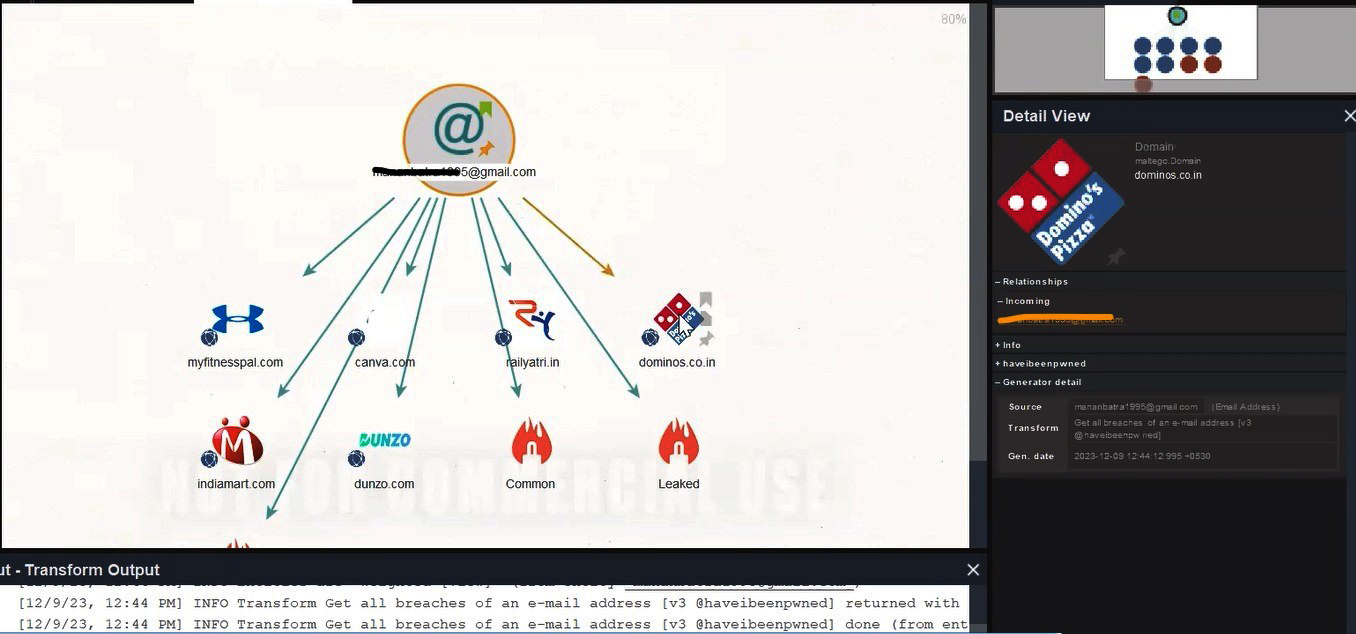
With a continuous aim of knowledge enhancement, Dridhg Security International Private Limited, conducted an OSINT Workshop – Social Media Intelligence and Digital Footprint Analysis on 1 December 2023. It was open to all – from students to research analysts, risk analysts operating in Security Operating Centres (SOCs), law enforcement personnel, to senior citizens. It was well received with employees of prominent organizations such as VFS Global, Vedanta Limited, UPL Limited, NetApp, and Mondelez. In fact, a repeat session also saw entrants from prominent Indian investigation companies.
A case study was discussed where incessant internet searches led to the arrest of an alleged murderer this year. We attempted the digital footprint analysis of the Instagram posts of the late actor Matthew Perry. Tools and techniques were also a prominent part of this workshop where the participants were introduced to AI software, which made image searches much more specific than one using search engines.
What a lot of people do not realize is that by helping in fraud detection OSINT tools and techniques help in fraud prevention. And while it is relevant for the security and risk consulting fields, given that internet safety and cyber security awareness is relevant for students and senior citizens alike, it is a pertinent subject in which all should have some level of understanding, if not expertise. By investing some time, it is possible to verify whether an email id, phone number, or a message which is floated on your devices is genuine or not. One can easily figure out the intention of the person who is communicating with you online. For instance, a few months ago, a contact was established by a person who claimed to be the ‘Crown Prince of Egypt’ on Linkedin. It took me just some cues and time to find the official Linkedin page of the real ‘Crown Prince of Egypt.’ Interestingly now fraudsters are also using bots and AI for social engineering. Celebrities like Tom Hanks and Ratan Tata have warned users not to believe in fake news created by their AI versions. Companies like Boat and Netflix too educate users about their authentic sites. There are some observations which suggest that a site or email or message is untrustworthy.
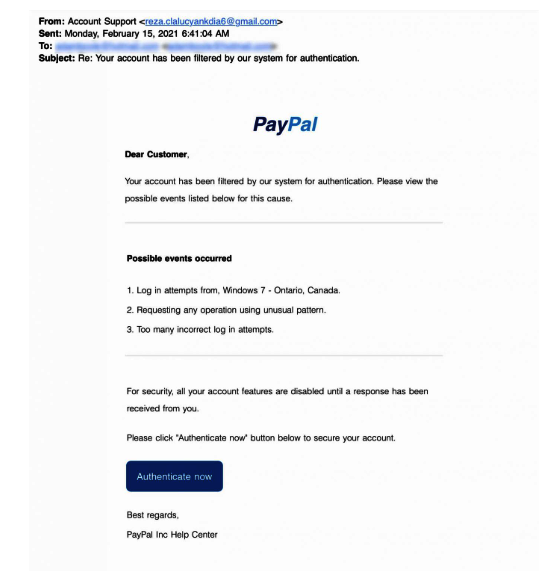
Some tips to spot a phishing email or message are as follows:
- Suspicious domain name –
- The email that is sent from a public email domain instead of an official email domain.
- A misspelled domain name
- The message is not articulate and is poorly written. One might notice some grammatical errors.
- The email or text might contain a suspicious attachment or links.
- Usually there is a sense of urgency indicated in the email or message. This is because the fraudster wants you to act before you can think.
Social Media Intelligence, in particular, is a double-edged sword. We are not the only ones reading about others. Others are also watching us. In fact, fraudsters use social engineering tools like creating a shortened URL link which is either shared along with some text or embedded in an image. The moment their target clicks on such a link, the fraudster gets a lot of information about the target which can include the target’s exact GPS location, compromising the target’s privacy. The same social engineering tools can also be used by a tech-savvy person to try to find details about, lets say, a catfish. Catfish is a term used to refer to a person who pretends to be someone else online and communicates under false pretense.
Considering the increasing number of cyber frauds, the chances of anyone becoming a target are high. Whether or not you become a victim totally depends on how aware and careful you are in protecting yourself from such attacks and fraudsters. And that is where the OSINT tool and technique becomes useful. There are multiple software tools, for instance, which can analyze emails, and websites and provide information whether such platforms have been compromised. Many times, email ids and even passwords get leaked on the dark web. In online workshops offered by DridhG Security International Private Limited, we try to educate the participants about reliable tools and techniques.
We need to be aware how open-source intelligence is being used, how it can be used and how it should or should not be used.
