
Capt SB Tyagi
Chief Councillor of ICISSM
As Warren Buffet said, “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.” A single act of crime on your property could diminish your brand. Hotels need to partner with an experienced physical security provider, and ensure that the entire staff understands the need to keep security top of mind – always. Savvy hoteliers should consider the following solutions when looking to improve their property’s security.
Meet and Greet
One of simplest, but most effective, ways of securing a property is to provide excellent customer service. “Engage customers you encounter,” Clifton said, “Ask them about their stay and if there’s anything you can do to help. You don’t have to throw more labour at security. Just make employees a little smarter.”
Meet and greet is the policy and program which efficient hotels deploy now a days and their happy stories depend more and more on its success! It takes management closer and closer to ‘Predictive Profiling’ which seems to be a panacea for many of the evils plaguing security.
What is Predictive Profiling?
It is a method of situational threat assessment designed to predict and categorize the potential for inappropriate, harmful, criminal and/ or terrorist behaviour that leads to the deployment of procedures and actions necessary to confirm, reduce and/ or eliminate such threats. It is the best practicable methodology for criminal/ terrorist threat mitigation. And the only method that adheres to legal, commercial and civil liberty concerns while still offering an effective security solution.

It categorizes threat based on the predicted methods of operation that would be used by a given aggressor to attack a given protected environment. A person holding a box cutter on a train going 100 miles per hour presents a threat in the form of hijacking a train while in transit. However, holding a box cutter in the middle of a train station is not threatening from the point of view of a masscasualty terrorist attack.
Whether it involves people or objects, every situation is evaluated according to time, location, and the possible threatening scenarios associated with the specific protected environment.
Predictive profiling as a threat assessment technique
The Predictive profiling helps predict and categorize potential criminal/ terrorist, their methods of operations based on behaviour, information and situation. It isn’t out of the box thinking but has its moorings in the observation skills of eagle eyed police officers who used to naturally scan people moving in queues and pick up the ones showing palpable signs of nervousness or physical indicators with a fairly good success rate. As a full-fledged art, Predictive Profiling is a focusing technique to spot the telltale signs of a crime/ criminal in the making.
Predictive profiling or Pro Active Threat Assessment is a way of surveillance from a criminal/ terrorist’s mind-set. The technique looks for suspicious indicators in the various stages of life cycle of a crime. The crime does not happen overnight and what we fight back or makes headline is just the tip of the iceberg.
According to Wikipedia, “Predictive profiling is a method of threat assessment designed to predict and categorize the potential for criminal and/ or terrorist methods of operation based on an observed behaviour, information, a situation and/ or objects.”
Predictive profiling offers a unique approach to threat mitigation
It begins from the point of view of the aggressor/ adversary and is based on actual adversary’s methods of operation, their modus operandi. This method is applicable to securing virtually any environment and to meeting any set of security requirements. In Predictive Profiling, one uses only the operational profile (not racial or statistical profile) of a terrorist or criminal as the basis for identifying suspicion indicators in a protected environment. When predictively profiling a situation, person or object, one identifies suspicion indicators that correlate with an adversary’s method of operation. For example, if a security officer observes a person walking with an empty suitcase in an airport (the suitcase appears very light; it bounces off the floor) he may identify this suspicious behaviour as an indication of a possible terrorist or criminal method of operation because:
- The person may be involved in theft or shop lifting (using the empty suitcase to stash what he would steal).
- The person may be involved in surveillance activities (the suitcase is only a prop to fit the airport environment).
- The person has dropped a bomb somewhere in the airport and is now exiting. Predictive Profiling explains that an act of crime or terror has the following stages/ episodes:
- Marking of the target.
- Intelligence gathering.
- Surveillance.
- Planning.
- Tooling up.
- Rehearsing and training.
- Execution, and
- Getaway.
Predictive Profiling in Hotel Industry
As having been largely successful in aviation security, similar profiling templates are created by the hotel industry. Passport officials scrutinize guests, applicants while on lookout for ubscrupulous elements. Israel, where the concept of Predictive Profiling is said to have originated along with USA, Netherland and host of other countries are pioneering its use.
Recall the 26/ 11 Mumbai Attacks and David Colman Headly’s testimony. He did eight hostile resonance of Mumbai, entered and left the country at will, joined an upscale gym and befriended people in the city without raising suspicion. He carried back photos, videos and GPS locations of Taj Hotel, Oberoi Hotel, State Police HQ and Bhabha Atomic Research Centre for his handlers to create a ‘Mock Up’ in Pakistan. He filmed the entire Bhagat Singh Marg (Colaba), Leopold Café and Taj Hotel for hours and yet we failed to get the ‘suspicion’ and prophesy correctly.
In our fight to catch up with terrorists, predictive profiling, complimentary to existing security measures is like an intelligent algorithm generating red flags for the outliers and help keep them at bay. Going ahead, we need to fight the war on terror intelligently, reinvent and reposition ourselves on that all-out offensive.
Alert to safety issues like never before, major hotels in the country are upping their security quotient in a big way. In fact, the hospitality industry’s apex body, the Hotel Association of India (HAI), with the biggest chains (the Taj, Oberoi and ITC, among others) in the country as members, has arrived at a complete list of security measures.
“We had been in continuous discussions and wanted to arrive at recommendations for both big properties that can afford the kind of investment needed and smaller ones which can’t afford some of these hi-tech measures,” said Priya Paul, Chairperson, Apeejay Surrendra Park Hotels.
A document made available to Business Standard recommends a list of measures. For external access control, for instance, the list recommends limiting access through a three-tier security ring outside all hotels (including putting up hydraulically-operated road barriers or retractable bollards, for premium properties) putting up CCTVs in public areas and at the entrances, and scanning not just the guest baggage but also all hotel supplies (fresh and otherwise), randomly opening some of those packages.
Guidelines also include guest profiling (systems in hotels to be linked to the Ministry of Home Affairs’ Watch List so that details such as a guest’s nationality, passport and visa numbers can be verified) and restricting access to different parts of the hotel through advanced technology. http://www.rediff. com/money/2008/dec/24security-guidelines-for-india-hotels.htm
Adversarial Methods of Operation (AMO)
Predictive Profiling uses the method of attack and it’s correlating Suspicion Indicators as the basis for threat assessment. The method of attack, from a pickpocket to a terrorist, remains constant and it includes the marking to getaway stages.
Suspicion Indicators
A suspicion indicator is an indication based on known (or predicted) terrorist or criminal methods of operation or deviation from a typical profile that may lead one to believe that an observed situation (persons and/ or objects) may have the potential for harming the protected environment and its inhabitants.
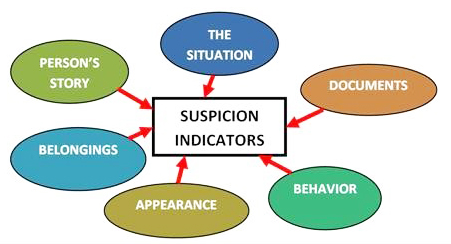
These indicators are derived from any aspect that relates to what we broadly term behaviour. This would include among other things attire, accent, affect, identity both as reflected in an individual’s documentation and by whom they say they are, their ‘cover story.’
Because suspicion indicators correlate directly with the AMOs associated with a given protected environment, there is no single definitive list. There are infinite examples of suspicion indicators, and perhaps the most poignant are those associated with the testimony of U.S. Airways agent Michael Tuohey, as regards the events of 9/11. Tuohey, who had worked for the airlines for over 30 years, 18 of which in Portland, checked in Mohamed Atta and Abdulaziz al-Omari who were flying from Portland, ME to Boston, MA. He noticed the following suspicion indicators in Atta and al-Omari’s actions and behaviour on the morning of 9/11:
- The terrorists arrived to check in only 30 minutes before departure.
- Atta and Omari were meandering in the checkin area although their flight was due to depart in 30 minutes.
- Omari never responded verbally to questions asked by Mr. Touhey; he just shook his head.
- Atta was looking at Mr. Touhey with anger.
- Both terrorists carried a full fare business class ticket.
- The tickets for both terrorists were one way.
Knowing the method of attack or method of operation of the terrorist or criminal, we can be more threat-oriented in protecting our environment. It allows us to be able to identify situations, objects or people as suspicious in a context of the method. Sometimes Predictive Profiling is referred to as conducting a situational threat assessment.
Prioritizing Hotel Security
The goal of every hotel owner is to provide safe, secure accommodations, while also offering friendly customer service.
It’s crucial to have robust security measures in place that keep both your guests and employees safe. Not only does inadequate safety and security put the property and its guests at risk from problems like theft, but hotels can also be held liable for criminal acts committed on their property. One act of violence or crime against a guest can destroy a hotel’s reputation.
Update locks: Locks that can track who goes in and out of rooms can serve as a deterrent to theft. “When employees realize there’s an audit process on door security, it makes rooms less prone to theft,” Callaghan says. Other upgrades include automatic deadbolts, which can better prevent external threats from thieves, or systems that eliminate the need for master keys.
Key Card Access Review: With a few pieces of hardware and minor programming, it is possible for a criminal to gain undetectable entree to millions of key card protected hotel rooms. At a security conference, a hacker presented the vulnerabilities he discovered in hotel room locks by a major manufacturer whose devices are installed in about seven million hotel rooms internationally. The manufacturer answered this security breach and is working with customers to repair these faulty mechanisms with hardware retooling. Hotels need to ensure that their key card access systems are not vulnerable to hacking or unlawful access.
Make time for safety meetings: Perhaps as part of a regular meeting, schedule time to talk about guest safety. Part of this time could also be spent watching training videos such as those produced by Safety Source Productions. These videos, accompanied by handouts, are a low-cost way to share information about guest safety and can train employees about how to spot suspicious behaviour.
Monitor activity with software: Having closed-circuit television to monitor the property doesn’t matter too much if no one is looking at the monitors. Recent innovations in software have solved that problem. Coupled with software, video cameras can now recognize activity in an area and provide an alert. One example: the system can alert when there is activity in a valet parking area. Other options include using a third party to monitor the exterior of the hotel. Some of these systems have voice command capability, where operators can see and warn off people captured on surveillance.
Evaluate and improve – quickly: Darrell Clifton, director of security for the 1,572-room Circus Circus Reno Hotel and Casino in Nevada, conducts weekly reviews of the property and even has checklists for staff to ensure areas such as stairwells, are clean, safe, and well lit. “We concentrate on our liability,” Clifton said, “If we know of something that’s happened, if someone was robbed or there was an accident, that area is quickly addressed. We can’t ignore it. We do something immediately to protect from another event happening.”
Engage With Your Guests: Maintain hotel security by encouraging your staff to be not only friendly and courteous with guests, but to also take an interest and get to know them when appropriate. You have the opportunity to meet people from all walks of life in the hotel business, and may potentially spot any nefarious characters if you get involved.
Always Check Credentials: Train your staff to verify the identity of every contractor that walks onto your property, whether they’re delivering flowers or fixing a sink. Make sure you thoroughly check the background of any contract partners as well, such as security officers or landscapers.
Control After-Hours Access: There’s a balance between customer service and hotel security; your guests should feel both welcome and safe. Station security personnel at all your property’s main access points during the off-hours and train them to both greet guests and turn away anyone that doesn’t have business there. A 24-hour security presence is a great deterrent to those who are up to no good.
Monitor Your Closed-Circuit Television: It’s not enough to just install cameras; make sure to check them, too. There are activity-activated cameras that issue an alert when there’s activity somewhere there shouldn’t be, or you might hire a third party to monitor your cameras. Some systems have voice-command capabilities, meaning you can not only monitor, but also verbally warn people off.
Security Officers that Welcome and Protect
Hotels must foster an inviting atmosphere for guests while ensuring safety and security. Presenting security personnel in a customer service role with officers dressed in upscale business clothing rather than traditional police or military style uniform, makes for a more accessible presence. This careful balance of customer service and security requires experience, specialized training and supervision. When your guests feel that they are both welcome and watched-over, they will feel more comfortable.
Ensuring that the right type of person occupies this customer-centric security role is also important. It is important to identify candidates through selective recruiting resources like hospitality and concierge associations and conduct extensive interviewing to ensure they possess a high aptitude for customer interaction.
Use of Technology in Profiling
In security and homeland security management, a strong emphasis is placed on technology – CCTV cameras, detection devices, scanners and the like. And while technology has its place, note that there are no known instances of a terrorist being caught using detection technology alone. Predictive Profiling is more concerned with identifying intent than a weapon. A well trained and motivated criminal or terrorist is capable of death and destruction using improvised weapons. Just as an individual with a potentially lethal weapon who has peaceful intentions, does not pose a threat.
Commitment to Ongoing Training
Security professionals require continual quality training if they are to be as responsive and knowledgeable as possible. Given that security personnel are placed in the front line of an hotelier’s security force, it is vital that they have all the latest tools needed to handle emergency and crisis situations. Security professionals should be able to access training in a way that benefits their lifestyle whether it is online or classroom training.
Hotels are held to extraordinarily high standards with regard to safety and security. It is critically important that all hotel staff be trained on appropriate security procedures for all high traffic areas including the lobby, front desk, baggage storage area, guest entry points, valet, and parking lot and receiving dock areas. The open environment fostered by hotels is welcoming to guests and visitors but, unfortunately, also creates vulnerabilities that must be addressed. Ensuring that all public spaces are continually monitored by staff and security personnel is crucial in maintaining a hospitable environment.
*View expressed in the article are solely of the Author
