
Milind Borkar – Expert Security Consultant
As technology evolves rapidly from year to year, it becomes a challenging task to determine the requirements to build a secure, robust and almost foolproof system that will fulfill all basic security parameters. These parameters will vary for each new system as the same parameters cannot be applied across the board for all systems. A robust system that meets the security requirements for any new and/ or green field project, the following points will drive the decision-making process.
Let’s use a CCTV system as an example:
- Budget and time available to implement the security system.
- Conduct a thorough site survey to determine security vulnerabilities and use it as vehicle to determine security requirements. This then becomes the primary driver along with the available budget.
- Detailed Camera information a. Mega-Pixel rating. b. Number of cameras required. c. Each camera location and it’s purposed function. d. Type of camera: Fixed, PTZ, indoor or outdoor, thermal performance, Field of View etc. e. Any other requirements that are specific to the location of the camera to fulfill its intended function.
- Storage capacity per camera – both inside as well as outside the camera.
- Storage architecture of the CCTV system.
- Network architecture of the CCTV system.
- Integration of other security components such as access control, perimeter intrusion detection systems, facial recognition, license plate recognition, under vehicle surveillance system, visitor management system, radar for areas not covered by cameras and other special requirements.
- Remote access/ cloud connectivity.
- Physical guarding.
- Video analytics.
- Vendor(s) selection.
As one can see there are several factors that influence the decision-making process in building a security system. We will briefly go over each one of them in the following sections:
Budget and time available
As in any and every sphere of life the available budget is the key factor. Based on the available budget and time, a determined effort needs to be put in place to first build a project specific requirements document. Several trade-offs will need to be considered if the project requirements cost exceeds the available budget. This could be an iterative process that will consume time and money in the planning phase. Each new or green field project or an update/ refresh cycle of an existing deployment must go through this elaboration process to avoid surprises in the implementation/ build phase.
Site survey
Conducting a site survey is the basis of building a security system. This phase is the most critical where a thorough site survey is conducted to determine security vulnerabilities. Along with this a determination needs to be made as to what other systems are required to complement the main CCTV system. The illustrative airport diagram should give a very good idea of the other security components that need to be explored. Once this information is gathered and documented, then this information becomes the driving force for subsequent phases of the project.
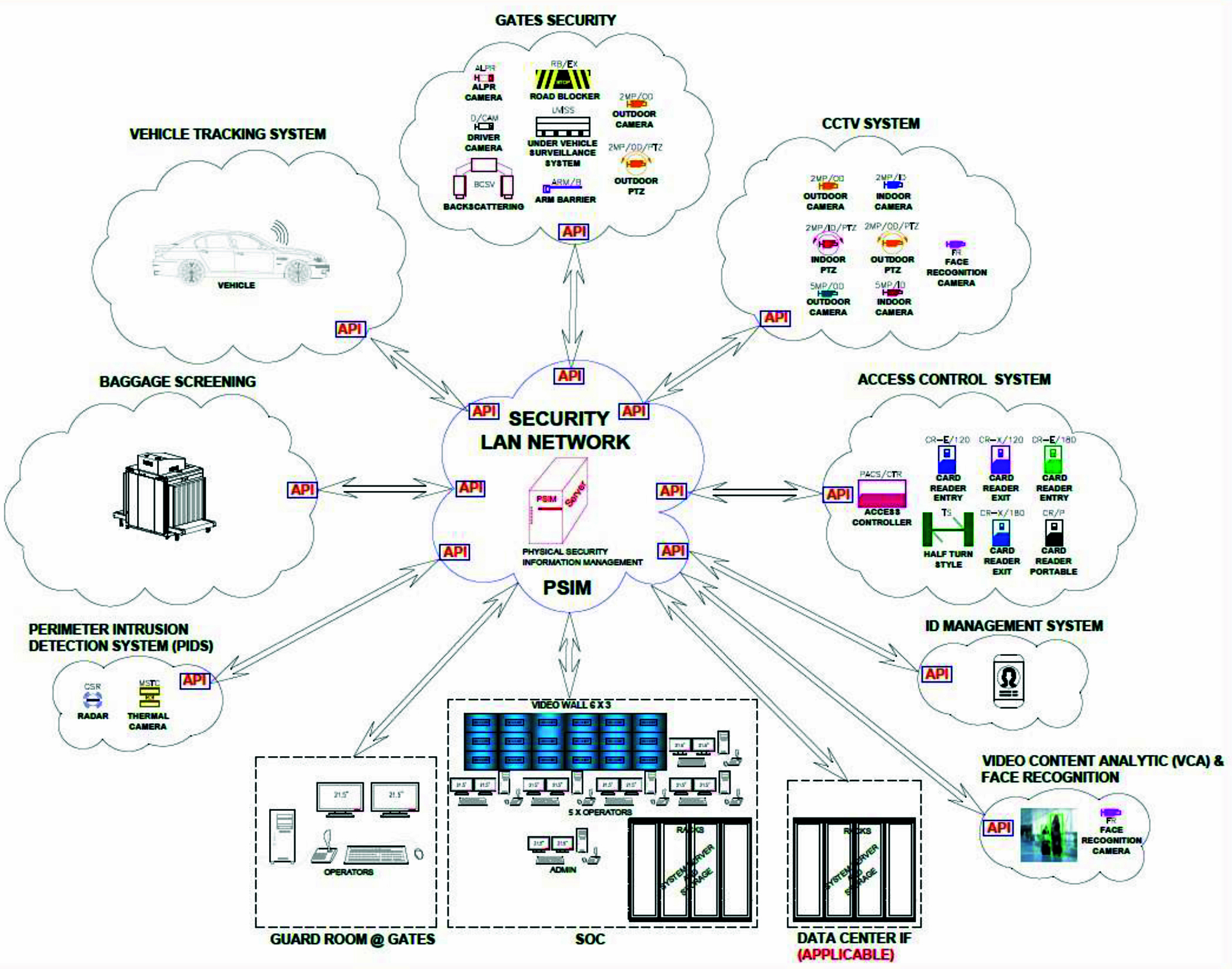
The best way to illustrate the process of building a security system is through an example. We are using an airport We will use the following diagram to highlight all the components that constitute a surveillance/ security system. We have used an airport as a use case. A typical airport is a super-set of any security deployment.
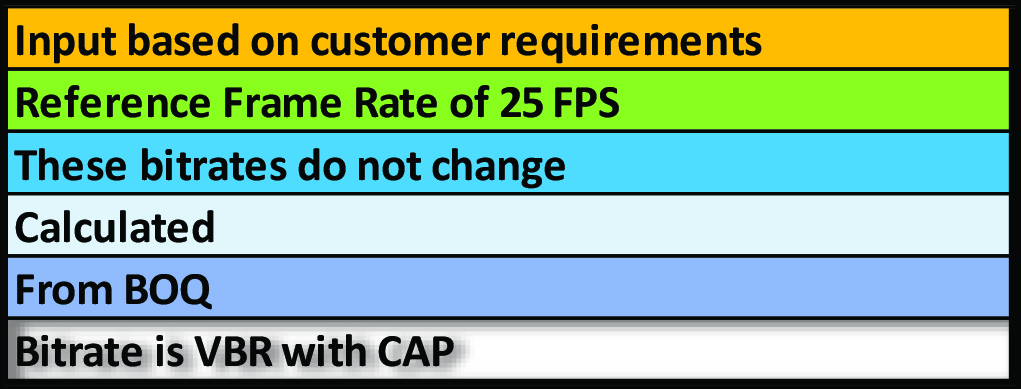
as an example as it has a super-set of inputs that can be applied to any security system design. The color-coded table is used to distinguish the various inputs/ requirements received from the customer.
The following table is a standard template that can be used to capture security requirements. These inputs are used to design the entire security system which can then be used to calculate the cost of the implementation.
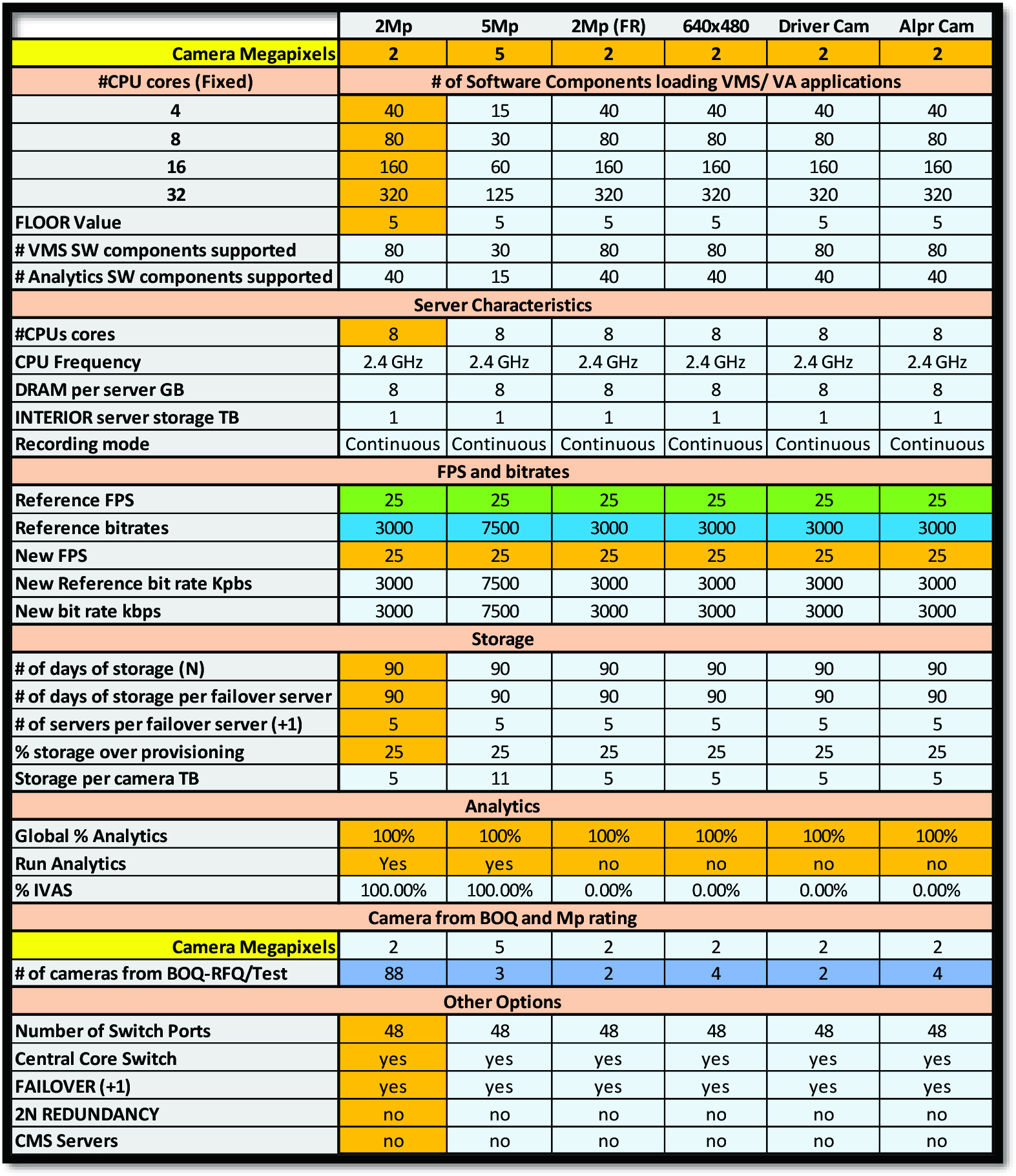
Using the above inputs from the customer and the respective BOQs for each airport, a complete design can be derived. The following table shows the output of the design process for 24 airports. Each airport has the same security requirements but BOQs are different.
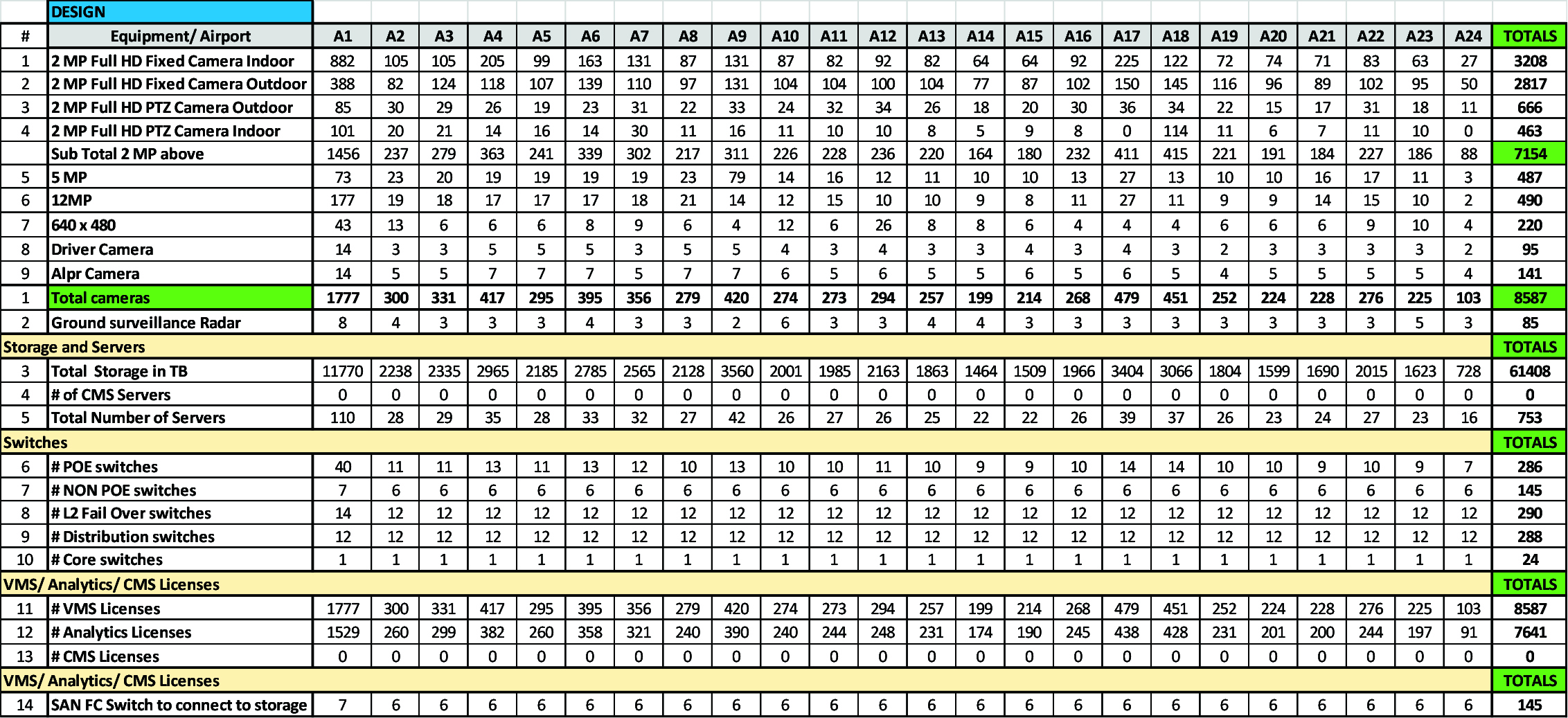
Once the design is completed to a 90% level of the target specification, the budgetary process can be started. Several vendors, RFQs etc. will be involved to go through an iterative process. This process will also vary for each geographical region. and must be considered. Without going into the details that vary for different geographical regions the important point to consider is the vendor selection process as it has a significant impact on the quality, robustness and overall cost of the system. Customers desirous of building a security system can engage subject matter experienced consultants who can guide and evaluate all the variables/ entities in the decision-making process.
Cost optimization through simulation
A security system design, implementation and build out are a complex system with many sub-systems that need to work with each other flawlessly. Every care must be taken in the early phases of the project as many variables are involved which can have a significant impact on the overall cost. One of the ways to help this process is to run a simulation based on the customer inputs.
Through experience we have determined the following:
- The customer knows what he wants but does not know how to get there.
- Almost all vendors over sell their products and services which do not benefit the customer in any way.
- A consultant is required in all cases to systematically guide and evaluate all the options available to provide the highest performance at the lowest cost to the customer.
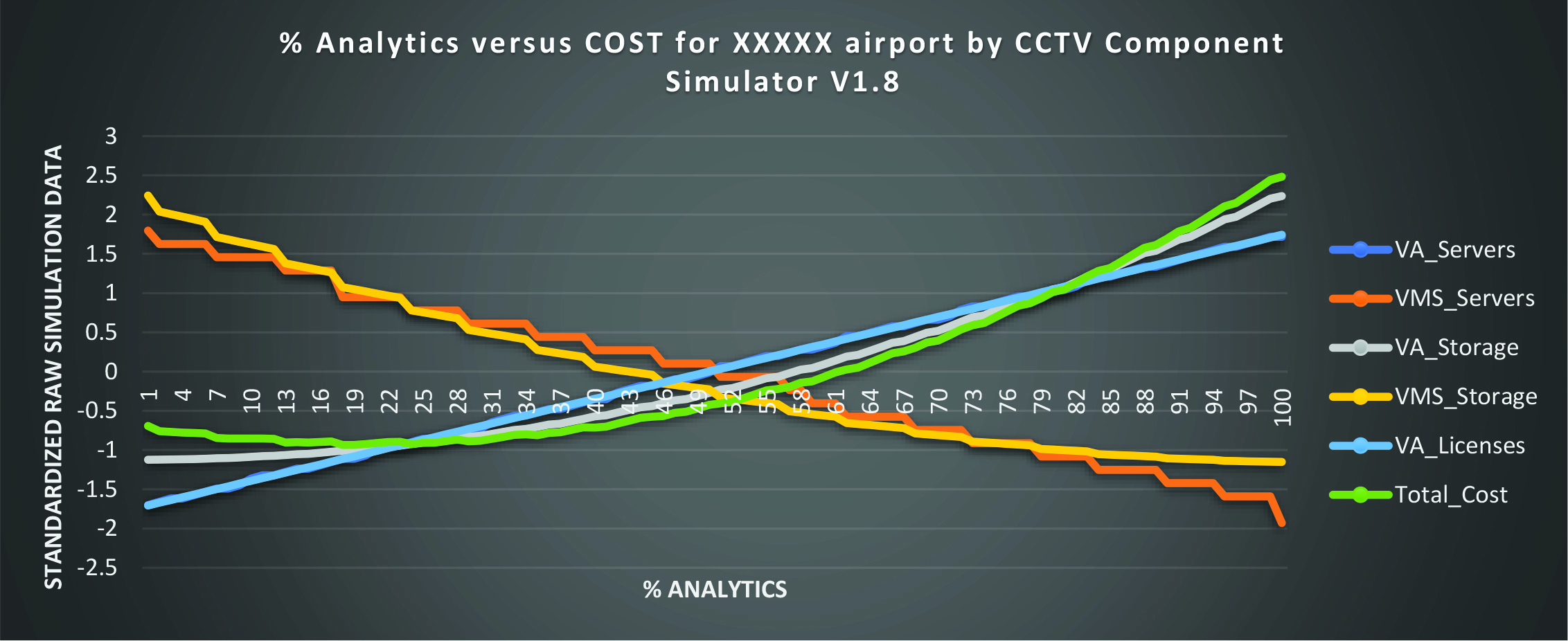
We will now go through a simulation for one of 24 airports. We will show how our simulator determines the highest performance at the lowest cost. The following graph il lustrates this. The X-Axis shows the percentage of cameras running video analytics (VA). The Y-AXIS shows the cost in a standardized format. The DELTA between the lowest cost and the highest cost is 3x. VA stands for Video Analytics; VMS stands for Video Management Software. The GREEN line is the overall COST with the other colored lines that sum up to the overall GREEN line cost.
Impact of Cost of Running Video Analytics for 24 airports
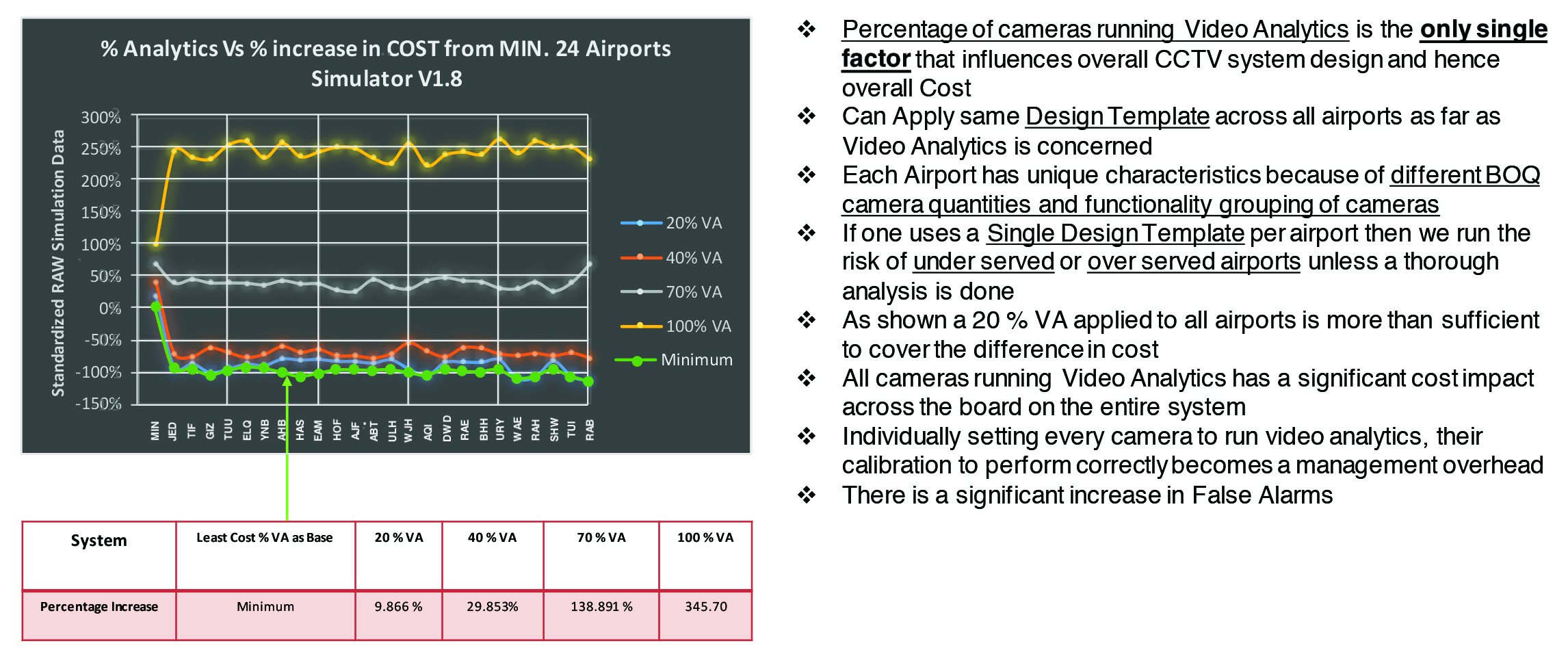
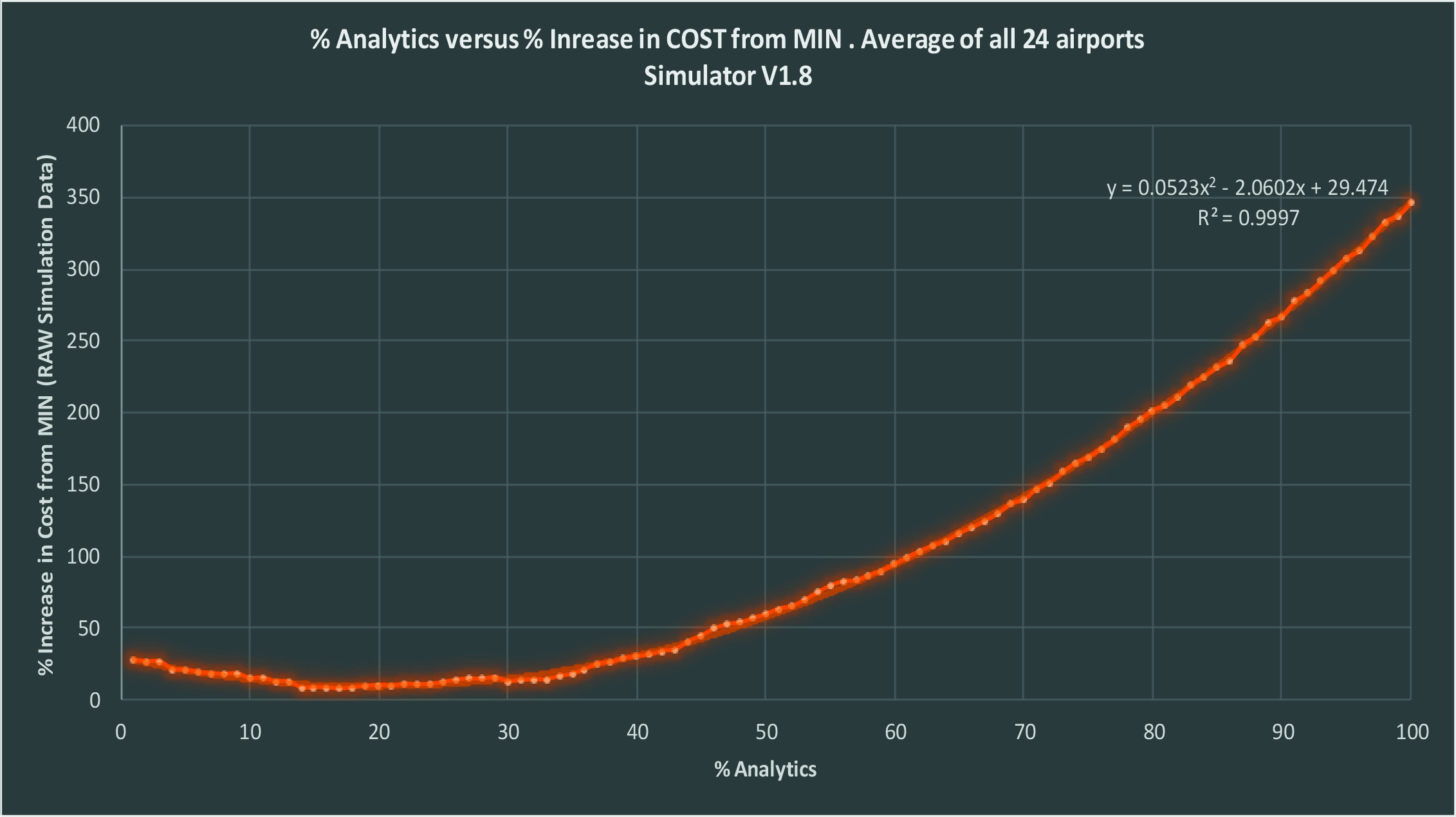
Cost Increases Exponentially as % VA increases from Simulation
Summary
- A surveillance/ Security system is a complex system comprising of several complex sub-systems.
- A complex system can and must be broken down into its sub-systems.
- An early iterative process is key to the longevity and success of the project.
An elaborate planning phase at the start of the project is crucial because many surprises will spring up if due diligence is not done in the planning phase. Poor planning can and will lead to budgetary disasters. Being penny wise and pound foolish is typical in the surveillance and security industry. We caution against this approach.
*Views expressed in the article are solely of the Author